Plugins
The functionality of Bareos can be extended by plugins. Plugins exist for the different daemons (Director, Storage- and File-Daemon).
To use plugins, they must be enabled in the configuration (Plugin Directory and optionally Plugin Names).
If a Plugin Directory is specified, Plugin Names defines which plugins get loaded.
If Plugin Names is not defined, all plugins found in the Plugin Directory are loaded.
The program bpluginfo can be used to retrieve information about a specific plugin.
Python Plugins
A special case of the Bareos Plugins are the Python Plugins. The Python plugins create a connection between the Bareos Plugin API and the Python programming language. With the Python plugins, it is possible to implement Bareos Plugins by writing Python code.
For each daemon there exists a Daemon Python Plugin which is a plugin implementing the C API for Bareos plugins, see python-fd Plugin, python-sd Plugin and python-dir Plugin.
This Python plugin can be configured via the usual plugin configuration mechanism which python files to load. The python files then implement the plugin functionality.
An example for such Python Plugins is the VMware Python Plugin.
With Bareos Version >= 23, the support of Python version 2 (which is end-of-life since Jan 1 2020) was removed.
The following plugins exist:
Python Version |
Python 3 |
|---|---|
Bareos File Daemon |
python3-fd |
Bareos Storage Daemon |
python3-sd |
Bareos Director |
python3-dir |
For implementation details see Python Plugin API.
Switching to Python 3
Switching to use the Python 3 plugin, the following needs to be changed:
Set Plugin Names = “python3” to make sure the Python3 plugin is loaded.
Adapt the Plugin setting in the fileset to use Python3: Plugin = “python3:module_name=…”
Recovering old backups
When doing backups, the plugin parameter string is stored into the backup stream. During restore, this string is used to determine the plugin that will handle this data.
To be able to restore backups created with Python plugins using the python3-fd plugin that were created using the python-fd plugin, the code determining the plugin that will handle the data also matches for the basename of the current available plugins without the last character.
So backups created with the python plugin (which uses Python 2) can be restored with the python3 plugin (which uses Python 3).
Warning
It is not possible to use the python plugin to restore backups created with the python3 plugin. Once switched, you need to stay on python3.
Director Plugins
python-dir Plugin
The python-dir (or python3-dir) plugin is intended to extend the functionality of the Bareos Director by Python code. Configuration:
install the bareos-director-python-plugin package
configure the
Plugin Directory (Dir->Director)activate the plugin in the Bareos Director configuration (
Plugin Names (Dir->Director))configure the plugin via
Dir Plugin Options (Dir->Job)restart the Bareos Director
The director plugins are configured in the Dir Plugin Options (Dir->Job) (or JobDefs resource).
To load a Python plugin you need
- instance
default is ’0’, you can leave this, as long as you only have 1 Director Python plugin. If you have more than 1, start with instance=0 and increment the instance for each plugin.
- module_name
The file (or directory) name of your plugin (without the suffix .py)
- module_path
Plugin path (optional, only required when using non default paths)
Plugin specific options can be added as key-value pairs, each pair separated by ’:’ key=value.
Single Director Python Plugin Example:
Multiple Python Plugin Loading Example:
Write your own Python Plugin
The class-based approach lets you easily reuse code already defined in the Python base class, which ships with the bareos-director-python-plugin package.
Some plugin examples are available on https://github.com/bareos/bareos/tree/master/contrib/dir-plugins, e.g. the plugin bareos-dir-nsca-sender, that submits the results and performance data of a backup job directly to Icinga or Nagios using the NSCA protocol.
Storage Daemon Plugins
autoxflate-sd
This plugin is part of the bareos-storage package.
The autoxflate-sd plugin can inflate (decompress) and deflate (compress) the data being written to or read from a device. It can also do both.
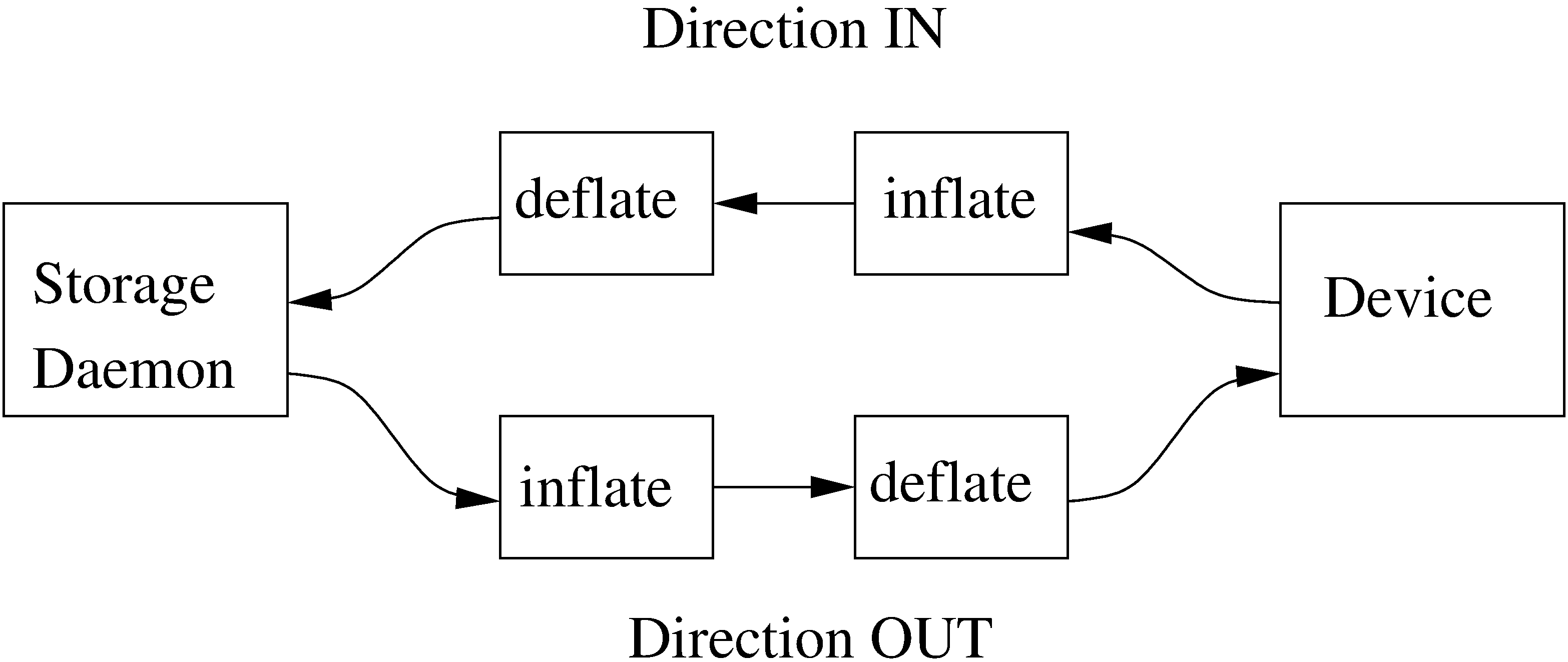
Therefore the autoxflate plugin inserts a inflate and a deflate function block into the stream going to the device (called OUT) and coming from the device (called IN).
Each stream passes first the inflate function block, then the deflate function block.
The inflate blocks are controlled by the setting of the Auto Inflate (Sd->Device) directive.
The deflate blocks are controlled by the setting of the Auto Deflate (Sd->Device), Auto Deflate Algorithm (Sd->Device) and Auto Deflate Level (Sd->Device) directives.
The inflate blocks, if enabled, will uncompress data if it is compressed using the algorithm that was used during compression.
The deflate blocks, if enabled, will compress uncompressed data with the algorithm and level configured in the according directives.
The series connection of the inflate and deflate function blocks makes the plugin very flexible.
Scenarios where this plugin can be used are for example:
client computers with weak cpus can do backups without compression and let the sd do the compression when writing to disk
compressed backups can be recompressed to a different compression format (e.g. gzip → lzo) using migration jobs
client backups can be compressed with compression algorithms that the client itself does not support
Multi-core cpus will be utilized when using parallel jobs as the compression is done in each jobs’ thread.
When the autoxflate plugin is configured, it will write some status information into the joblog.
Additional Auto XFlate On Replication (Sd->Storage) can be configured at the Storage resource.
python-sd Plugin
The python-sd plugin behaves similar to the python-dir Plugin.
scsicrypto-sd
This plugin is part of the bareos-storage-tape package.
General
LTO Hardware Encryption
Modern tape-drives, for example LTO (from LTO4 onwards) support hardware encryption. There are several ways of using encryption with these drives. The following three types of key management are available for encrypting drives. The transmission of the keys to the volumes is accomplished by either of the three:
A backup application that supports Application Managed Encryption (AME)
A tape library that supports Library Managed Encryption (LME)
A Key Management Appliance (KMA)
We added support for Application Managed Encryption (AME) scheme, where on labeling a crypto key is generated for a volume and when the volume is mounted, the crypto key is loaded. When finally the volume is unmounted, the key is cleared from the memory of the Tape Drive using the SCSI SPOUT command set.
If you have implemented Library Managed Encryption (LME) or a Key Management Appliance (KMA), there is no need to have support from Bareos on loading and clearing the encryption keys, as either the Library knows the per volume encryption keys itself, or it will ask the KMA for the encryption key when it needs it. For big installations you might consider using a KMA, but the Application Managed Encryption implemented in Bareos should also scale rather well and have a low overhead as the keys are only loaded and cleared when needed.
The scsicrypto-sd plugin
The scsicrypto-sd hooks into the unload, label read, label write and label verified events for loading and clearing the key. It checks whether it it needs to clear the drive by either using an internal state (if it loaded a key before) or by checking the state of a special option that first issues an encrytion status query. If there is a connection to the director and the volume information is not available, it will ask the director for the data on the currently loaded volume. If no connection is available, a cache will be used which should contain the most recently mounted volumes. If an encryption key is available, it will be loaded into the drive’s memory.
Changes in the director
The director has been extended with additional code for handling hardware data encryption. The extra keyword encrypt on the label of a volume will force the director to generate a new semi-random passphrase for the volume, which will be stored in the database as part of the media information.
A passphrase is always stored in the database base64-encoded. When a so called Key Encryption Key is set in the config of the director, the passphrase is first wrapped using RFC3394 key wrapping and then base64-encoded. By using key wrapping, the keys in the database are safe against people sniffing the info, as the data is still encrypted using the Key Encryption Key (which in essence is just an extra passphrase of the same length as the volume passphrases used).
When the storage daemon needs to mount the volume, it will ask the director for the volume information and that protocol is extended with the exchange of the base64-wrapped encryption key (passphrase). The storage daemon provides an extra config option in which it records the Key Encryption Key of the particular director, and as such can unwrap the key sent into the original passphrase.
As can be seen from the above info we don’t allow the user to enter a passphrase, but generate a semi-random passphrase using the openssl random functions (if available) and convert that into a readable ASCII stream of letters, numbers and most other characters, apart from the quotes and space etc. This will produce much stronger passphrases than when requesting the info from a user. As we store this information in the database, the user never has to enter these passphrases.
The volume label is written in unencrypted form to the volume, so we can always recognize a Bareos volume. When the key is loaded onto the drive, we set the decryption mode to mixed, so we can read both unencrypted and encrypted data from the volume. When no key or the wrong key has been loaded, the drive will give an IO error when trying to read the volume. For disaster recovery you can store the Key Encryption Key and the content of the wrapped encryption keys somewhere safe and the bscrypto tool together with the scsicrypto-sd plugin can be used to get access to your volumes, in case you ever lose your complete environment.
If you don’t want to use the scsicrypto-sd plugin when doing DR and you are only reading one volume, you can also set the crypto key using the bscrypto tool. Because we use the mixed decryption mode, in which you can read both encrypted and unencrypted data from a volume, you can set the right encryption key before reading the volume label.
If you need to read more than one volume, you better use the scsicrypto-sd plugin with tools like bscan/bextract, as the plugin will then auto-load the correct encryption key when it loads the volume, similarly to what the storage daemon does when performing backups and restores.
The volume label is unencrypted, so a volume can also be recognized by a non-encrypted installation, but it won’t be able to read the actual data from it. Using an encrypted volume label doesn’t add much security (there is no security-related info in the volume label anyhow) and it makes it harder to recognize either a labeled volume with encrypted data or an unlabeled new volume (both would return an IO-error on read of the label.)
Configuration of the scsicrypto-sd plugin
SCSI crypto setup
The initial setup of SCSI crypto looks something like this:
Generate a Key Encryption Key e.g.
bscrypto -g -
For details see bscrypto.
Security Setup
Some security levels need to be increased for the storage daemon to be able to use the low level SCSI interface for setting and getting the encryption status on a tape device.
The following additional security is needed for the following operating systems:
Linux (SG_IO ioctl interface):
To perform the operations required for scsicrypto, the programs must either run as user root or the additional capability CAP_SYS_RAWIO+EP (see capabilities(7)) must be set. The Bareos Storage Daemon normally runs as user bareos. Running it as root is not recommended.
If bareos-sd does not have the appropriate capabilities, all other tape operations may still work correctly, but you will get “Unable to perform SG_IO ioctl” errors.
Note
Since Version >= 21.0.1 package installation and upgrade will check for the presence of .enable-cap_sys_rawio in your bareos config dir and will configure the required capabilities.
If you want capabilities automatically set up during package install, you can just create /etc/bareos/.enable-cap_sys_rawio.
Before Version >= 21.0.1 it is mandatory to setup capabilities manually after each update (see below).
setcap binaries (recommended)
You can also set up the extra capability on bareos-sd, bcopy, bextract, bls, bscan, bscrypto, btape by running the following commands:
Set the setting with our helper
/usr/lib/bareos/scripts/bareos-config set_scsicrypto_capabilities
Set the setting manually
setcap cap_sys_rawio=ep /usr/sbin/bareos-sd
setcap cap_sys_rawio=ep /usr/sbin/bcopy
setcap cap_sys_rawio=ep /usr/sbin/bextract
setcap cap_sys_rawio=ep /usr/sbin/bls
setcap cap_sys_rawio=ep /usr/sbin/bscan
setcap cap_sys_rawio=ep /usr/sbin/bscrypto
setcap cap_sys_rawio=ep /usr/sbin/btape
Remove the setting with our helper
/usr/lib/bareos/scripts/bareos-config unset_scsicrypto_capabilities
Remove the setting manually
setcap -r /usr/sbin/bareos-sd
setcap -r /usr/sbin/bcopy
setcap -r /usr/sbin/bextract
setcap -r /usr/sbin/bls
setcap -r /usr/sbin/bscan
setcap -r /usr/sbin/bscrypto
setcap -r /usr/sbin/btape
Check the setting with our helper
/usr/lib/bareos/scripts/bareos-config check_scsicrypto_capabilities
Check the setting manually
getcap -v /usr/sbin/bareos-sd
getcap -v /usr/sbin/bcopy
getcap -v /usr/sbin/bextract
getcap -v /usr/sbin/bls
getcap -v /usr/sbin/bscan
getcap -v /usr/sbin/bscrypto
getcap -v /usr/sbin/btape
getcap and setcap are part of libcap-progs.
Warning
Adding capabilities like cap_sys_rawio to binaries can increase their abuse. We also recommend to restrict a bit more their ownership to root as owner and bareos as group, plus setting chmod to 0750. Doing so will restrict execution root and members of group bareos. All these steps are done for you by our helper.
systemd (not recommended)
To add the capabilities to bareos-sd.service you can add in file /etc/systemd/system/bareos-sd.d/override.conf a section containing the AmbientCapabilities=CAP_SYS_RAWIO line.
The easiest way to create this file is to use the following instructions as root.
systemctl edit bareos-sd.service
Fill the file with the following content, then save and exit
### Editing /etc/systemd/system/bareos-storage.service.d/override.conf
### Anything between here and the comment below will become the new contents of the file
[Service]
AmbientCapabilities=CAP_SYS_RAWIO
Reload systemd configuration and restart bareos-sd
systemctl daemon-reload
systemctl restart bareos-sd
systemctl status bareos-sd
● bareos-storage.service - Bareos Storage Daemon service
Loaded: loaded (/lib/systemd/system/bareos-storage.service; enabled; vendor preset: enabled)
Drop-In: /etc/systemd/system/bareos-storage.service.d
└─override.conf
Active: active (running) since Tue 2022-02-01 15:12:49 CET; 5s ago
Docs: man:bareos-sd(8)
Main PID: 11142 (bareos-sd)
Tasks: 2 (limit: 2298)
Memory: 1.1M
CPU: 8ms
CGroup: /system.slice/bareos-storage.service
└─11142 /usr/sbin/bareos-sd -f
systemd[1]: Started Bareos Storage Daemon service.
To check status of capabilities of the running daemon you can use the getpcaps followed by the pid of bareos-sd.
root:~# getpcaps 11142
11142: cap_sys_rawio=eip
Warning
As of systemd version 249 There’s no mechanism to pass restricted flag (+ep), so the result will always be full CAP_SYS_RAWIO (eip)
Solaris (USCSI ioctl interface):
The user running the storage daemon needs the following additional privileges:
PRIV_SYS_DEVICES (see privileges(5))
If you are running the storage daemon as another user than root (which has the PRIV_SYS_DEVICES privilege), you need to add it to the current set of privileges. This can be set up by setting this either as a project for the user, or as a set of extra privileges in the SMF definition starting the storage daemon. The SMF setup is the cleanest one.
For SMF make sure you have something like this in the instance block:
Changes in bareos-sd configuration
Set the Key Encryption Key
Enable the loading of storage daemon plugins
Enable the SCSI encryption option
Enable this, if you want the plugin to probe the encryption status of the drive when it needs to clear a pending key
Changes in bareos-dir configuration
Set the Key Encryption Key
Testing
Restart the Storage Daemon and the Director. After this you can label new volumes with the encrypt option, e.g.
Disaster Recovery
For Disaster Recovery (DR) see Restore Bareos Server, you need the following information:
Actual bareos-sd configuration files with config options enabled as described above, including, among others, a definition of a director with the Key Encryption Key used for creating the encryption keys of the volumes.
The actual keys used for the encryption of the volumes.
This data needs to be available as a so called crypto cache file which is used by the plugin when no connection to the director can be made to do a lookup (most likely on DR).
Most of the times the needed information, e.g. the bootstrap info, is available on recently written volumes and most of the time the encryption cache will contain the most recent data, so a recent copy of the bareos-sd.<portnr>.cryptoc file in the working directory is enough most of the time. You can also save the info from database in a safe place and use bscrypto to populate this info (VolumeName → EncryptKey) into the crypto cache file used by
bextract and bscan. You can use bscrypto with the following flags to create a new or update an existing crypto cache file e.g.:
bscrypto -p /var/lib/bareos/bareos-sd.<portnr>.cryptoc
A valid BSR file containing the location of the last safe of the database makes recovery much easier. Adding a post script to the database save job could collect the needed info and make sure its stored somewhere safe.
Recover the database in the normal way e.g. for postgresql:
bextract -D <director_name> -V <volname> /dev/nst0 /tmp -b bootstrap.bsr /usr/lib/bareos/scripts/create_bareos_database /usr/lib/bareos/scripts/grant_bareos_privileges psql bareos < /tmp/var/lib/bareos/bareos.sql
Or something similar (change paths to follow where you installed the software or where the package put it).
Note
As described at the beginning of this chapter, there are different types of key management, AME, LME and KMA. If the Library is set up for LME or KMA, it probably won’t allow our AME setup and the scsi-crypto plugin will fail to set/clear the encryption key. To be able to use AME you need to “Modify Encryption Method” and set it to something like “Application Managed”. If you decide to use LME or KMA you don’t have to bother with the whole setup of AME which may for big libraries be easier, although the overhead of using AME even for very big libraries should be minimal.
scsitapealert-sd
This plugin is part of the bareos-storage-tape package.
The plugin retrieves TapeAlert flags of every Device (Sd) that
has Drive Tape Alert Enabled (Sd->Device) set.
For every flag set, a detailed message will be written to the joblog.
The plugin directly queries the TapeAlert page from the device.
This requires raw access to the device.
On Linux, when the Bareos Storage Daemon is run as a normal user (the default), the process
needs the capability CAP_SYS_RAWIO to facilitate this.
The Security Setup section of the plugin scsicrypto-sd
explains how to set this up.
Note
When you see the error message
Unable to perform SG_IO ioctl on fd X: ERR=Permission denied your Bareos Storage Daemon
probably lacks the CAP_SYS_RAWIO capability.
File Daemon Plugins
File Daemon plugins are configured by the Plugin directive of a File Set.
Warning
Currently the plugin command is being stored as part of the backup. The restore command in your directive should be flexible enough if things might change in future, otherwise you could run into trouble.
Apache Libcloud Plugin
The Libcloud plugin can be used to backup objects from cloud storages via the Simple Storage Service (S3) protocol. The plugin code is based on the work of Alexandre Bruyelles.
Status of Libcloud Plugin
The status of the Libcloud plugin is experimental. It can automatically recurse nested Buckets and backup all included Objects on a S3 storage. However, restore of objects cannot be done directly back to the storage. A restore will write these objects as files on a filesystem.
Since Version >= 25.0.0 the plugin was changed to use the Python threading module instead of multiprocessing to make it work with current Python versions. Unfortunately libcloud is not fully thread safe, this can cause unresponsive worker threads on bad network connections when libcloud calls run into timeouts. The plugin code tries to handle that in a reasonable way, but especially when the option fail_on_download_error is disabled, this can cause the plugin to hang indefinetely and would require restarting the bareos-filedaemon. So the default and recommended setting for is option is now disabled.
Warning
It is recommended to use the grpc plugin mode, especially when running multiple jobs with the Libcloud plugin in parallel.
Requirements of Libcloud Plugin
To use the Apache Libcloud plugin, the apache-libcloud module for Python 3 must be installed.
The plugin needs several options to run properly, plugin options can be set as explained in python-fd Plugin.
Installation of Libcloud Plugin
The installation is done by installing the package bareos-filedaemon-libcloud-python-plugin.
Configuration of Libcloud Plugin
The plugin options, separated by a colon:
- module_path
Path to the bareos modules (optional)
- module_name=bareos-fd-libcloud
This is the name of the plugin module
- config_file
The plugin needs additional parameters, this is the path to the config file (see below)
- buckets_include
Comma-separated list of buckets to include in backup
- buckets_exclude
Comma-separated list of buckets to exclude from backup
And the job as follows:
And the plugin config file as follows:
Note
Do not use quotes in the above config file, it is processed by the Python ConfigParser module and the quotes would not be stripped from the string.
Mandatory Plugin Options:
These options in the config file are mandatory:
- hostname
The hostname/ip address of the storage backend server
- port
The portnumber for the backend server
- tls
Use Transport encryption, if supported by the backend
- provider
The provider string, ‘S3’ being the default if not specified
- username
The username to use for backups, in S3 terminology this is the access key
- password
The password for the backup user, in S3 terminology this is the secret key
- nb_worker
The number of worker processes who can preload data from objects simultaneously before they are given to the plugin process that does the backup
- queue_size
The maximum size in numbers of objects of the internal communication queue between the processes
- prefetch_size
The maximum object size in bytes that should be preloaded from the workers; objects larger than this size are loaded by the plugin process itself. Note that disk space consumption can be up to queue_size times the value of this option. Files up the size of this options setting are downloaded in parallel by the worker threads, which can significantly reduce the job run time. Larger files will be sequential streaming downloads.
- temporary_download_directory
The local path where the worker processes put their temporarily downloaded files to; the filedaemon process needs read and write access to this path
Optional Plugin Options:
These options in the config file are optional:
- fail_on_download_error
When this option is enabled, any error during a file download will fail the backup job. This is the default and recommended as explained above. When disabling this setting by fail_on_download_error = no, a warning will be issued on each failure and the next file will be backed up. As mentioned above, this can lead to unresponsive worker threads on bad network connections, so it’s not recommended to set this to disabled.
- job_message_after_each_number_of_objects
When running a backup, put a jobmessage after each count of “job_message_after_number_of_objects” to the joblog or no message if parameter equals 0; default is 100.
- prefetch_inmemory_size
The maximum object size in bytes that should be preloaded from the workers into memory; objects larger than this size are loaded by the plugin process itself. The default value is 10240 (10KB). The value should be smaller than the value of the prefetch_size option.
- global_timeout
Global timeout in seconds, as mentioned in the Status of Libcloud Plugin section above, it could happen on bad network connections that libcloud calls cause hanging worker threads. With this timeout setting the plugin tries to terminate the job with error when it can detect this state. Default value is 600 seconds.
- libcloud_timeout
Timeout value for single libcloud calls in seconds, default value is 60.
Barri Plugin
The Barri Plugin can create disaster recovery images of computers running the Windows operating system. Barri stands for Bareos Recovery Imager and is a tool collection for creating Windows disaster recovery images and for recovering Windows Computers:
Barri offers a variety of options to create and recover barri disaster recovery images.
The Barri Plugin for the Windows Filedaemon is the most common way of creating barri images.
Backup operation
A Computer running the Bareos Filedaemon with the Barri plugin can create a disaster recovery image out of the running Computer without interfering with the normal operation.
A second option to create a barri disaster recovery file is to use the Windows commandline tool barri-cli.exe. As barri-cli.exe uses the exact same functionality to create the image as the plugin, it also creates the image during normal operation and does not require a shutdown of the computer or similar.
Restore operation
There are multiple options to recover a computer from a backup created with barri.
Two options use a linux live recovery system to recover the computer:
A Linux Filedaemon with the barri filedaemon plugin can be run inside of the linux live system. The Linux Live system needs to be configured to have network access and to start the linux filedaemon that needs to be connected to the bareos system. The recovery then is performed by running a bareos restore command restoring the barri backup directly to the attached disks inside of the live system.
The second option to recover a barri backup using a Linux Live Image is to recover the image via the barri-cli linux cli command. Therefore the existing .barri backup needs to be restored to a local file on the backup server first. This file then can be used to restore the computer from the linux commandline. The imagefile can be made available via removable media, network or any other means. Using the barri-cli makes a recovery possible in a complete disconnected environment.
In cases where linux does not have a driver that supports the hardware and thus the system drives are not visible from the linux system, there is a third option to recover the .barri file from the windows command line using barri-cli.exe for windows.
If you can connect your disk to another Windows computer (e.g. via portable disk case), you can recover the disk there.
If you need to run the recovery on the original computer, this option requires Windows PE, which is a live windows that can be created and preloaded with special drivers if required.
It is included in Bareos since Version >= 25.0.0.
Installation
- Linux
Install the package bareos-filedaemon-barri-plugin via your package manager (e.g. apt or dnf)
- Windows
Install the Windows installation package
Configuration of the Windows FD
Make sure to add or enable the following settings in your Windows Bareos File Daemon configuration:
After a restart of the bareos service on windows, the ouput of the status client command shows that the plugin was successfully loaded:
*status client=windowsdr-fd
[...]
windr-fd Version: 25.0.0~pre1046.c3bf07897 (29 September 2025) VSS Microsoft Windows 8 Professional (build 9200), 64-bit
Daemon started 01-Okt-25 10:01. Jobs: run=0 running=0, self-compiled binary
Sizeof: boffset_t=8 size_t=8 debug=0 trace=0 bwlimit=0kB/s
Plugin Info:
Plugin : barri-fd.dll
Description: This plugin allows you to backup your windows system for disaster recovery.
Version : 0.9.0 (Juli 2025)
Author : Sebastian Sura
License : Bareos AGPLv3
Usage : barri:unknown disks:unknown partitions:unknown extents:ignore disks=<disks to ignore>
unknown disks: try to save disks, that contain no snapshotted data
unknown partitions: try to save partitions, that contain no snapshotted data
unknown extents: try to save even unsnapshotted parts of partitions
disks to ignore: a comma-separated list of disk ids (i.e. '1,2,5') of disks
to not backup
[...]
Now a fileset and a job need to be configured on the bareos server. Make sure to set
in the fileset. The portable setting allows to recover the files also on Bareos File Daemon running on other OS than Windows. The VSS setting avoids an extra VSS snapshot that is not needed as barri does the VSS snapshot handling itself.
Note
Please be sure to set
the fileset option
Portable (Dir->Fileset->Include->Options) = yes, andthe fileset directive
Enable VSS (Dir->Fileset) = No.
Backup with the Windows barri-fd Plugin
Note
Currently it is not possible to recover a barri backup via the windows barri-fd plugin. For recovery use the linux plugin or one of the cli tools.
In order to make a backup, run the job defined above (barri) to make a disaster recovery image backup.
*run job=barri yes
*messages
[...]
[...] windr-fd JobId 1: Version: 25.0.0~pre1046.c3bf07897 (29 September 2025) Microsoft Windows 8 Professional (build 9200), 64-bit
[...] windr-fd JobId 1: setting up vss
[...] bareos-sd JobId 1: JustInTime Reservation: Finding drive to reserve.
[...] bareos-dir JobId 1: Created new Volume "Full-0001" in catalog.
[...] bareos-sd JobId 1: Using Device "FileStorage" (/var/lib/bareos/storage) to write.
[...] bareos-sd JobId 1: Labeled new Volume "Full-0001" on device "FileStorage" (/var/lib/bareos/storage).
[...] bareos-sd JobId 1: Moving to end of data on volume "Full-0001"
[...] bareos-sd JobId 1: Ready to append to end of Volume "Full-0001" size=223
[...] windr-fd JobId 1: creating a vss snapshot
[...] windr-fd JobId 1: ... done! (=> Id = {FE763C79-9FC4-429F-80A1-458EAA09FE54})
[...] windr-fd JobId 1: examining volume \\?\Volume{ea8f2bab-dd31-4ba5-aa39-482c24b2589e}\ (\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy8)
[...] windr-fd JobId 1: ... done!
[...] windr-fd JobId 1: examining volume \\?\Volume{106f2185-d422-407a-b928-198db1c4566d}\ (\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy9)
[...] windr-fd JobId 1: ... done!
[...] windr-fd JobId 1: examining volume \\?\Volume{5d9d24bf-b2fd-47a4-8577-594f29792d0e}\ (\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy10)
[...] windr-fd JobId 1: ... done!
[...] windr-fd JobId 1: collecting info from disk \\.\PhysicalDrive0
[...] windr-fd JobId 1: => recorded!
[...] windr-fd JobId 1: generating backup plan
[...] windr-fd JobId 1: disk 0/partition 1 has no snapshotted data => recorded (special-partition)
[...] windr-fd JobId 1: ... done!
[...] bareos-sd JobId 1: Releasing device "FileStorage" (/var/lib/bareos/storage).
[...] bareos-sd JobId 1: Elapsed time=00:16:57, Transfer rate=34.22 M Bytes/second
[...] bareos-dir JobId 1: Insert of attributes batch table with 2 entries start
[...] bareos-dir JobId 1: Insert of attributes batch table done
[...] bareos-dir JobId 1: Bareos bareos-dir 25.0.0~pre1074.e81033063 (01Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 1
Job: barri.2025-10-01_14.37.37_04
Backup Level: Full (upgraded from Incremental)
Client: "windowsdr-fd" 25.0.0~pre1046.c3bf07897 (29Sep25) Microsoft Windows 8 Professional (build 9200), 64-bit,Windows-x64
FileSet: "barri_fileset" 2025-10-01 14:37:37
Pool: "Full" (From Job FullPool override)
Catalog: "MyCatalog" (From Client resource)
Storage: "File" (From Job resource)
Scheduled time: 01-Okt-2025 14:37:37
Start time: 01-Okt-2025 14:37:39
End time: 01-Okt-2025 14:54:38
Elapsed time: 16 mins 59 secs
Priority: 10
Allow Mixed Priority: no
FD Files Written: 2
SD Files Written: 2
FD Bytes Written: 34,806,828,300 (34.80 GB)
SD Bytes Written: 34,806,828,529 (34.80 GB)
Rate: 34157,8 KB/s
Software Compression: 66,0 % (lz4)
VSS: no
Encryption: no
Accurate: no
Volume name(s): Full-0001
Volume Session Id: 3
Volume Session Time: 1759317946
Last Volume Bytes: 34,812,710,996 (34.81 GB)
Non-fatal FD errors: 0
SD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Backup OK
As the joblog tells us, two files have been backed up. With the command list files jobid=1 we can check what files have been backed up:
*list files jobid=1
[...]
@BARRI/windr-fd.barri
@BARRI/windr-fd.log
The plugin backed up two files:
windr-fd.barriThis is the .barri file containing the disaster recovery data itself.
windr-fd.logThis file contains a logfile that was recorded during the creation of the
.barrifile.
Restore with the Linux FD Plugin
Start Live Linux. In this example we use Fedora 42 Live Linux.
Install bareos-filedaemon and bareos-filedaemon-barri-plugin
Configure:
/etc/bareos/bareos-fd.d/client/myself.conf on linux live systemNow we need to determine to which devices we want to restore the backed up disks. This can be achieved by using the command lsblk which shows us the detected block devices of the computer:
lsblk to determine the target disk(s)NAME MAJ:MIN RM SIZE RO TYPE MOUNTPOINTS
loop0 7:0 0 2G 1 loop /run/rootfsbase
sda 8:0 1 117.2G 0 disk
├─sda1 8:1 1 2.2G 0 part /run/initramfs/live
└─sda2 8:2 1 30M 0 part
sdb 8:16 1 120.3G 0 disk
└─sdb1 8:17 1 120.3G 0 part /run/media/liveuser/SanDisk
zram0 251:0 0 8G 0 disk [SWAP]
nvme0n1 259:0 0 238.5G 0 disk
The demo system has currently two usb devices which show up as sda and sdb and a
nvme device shown as nvme0n1.
As the nvme0n1 has a size of 238.5G, it is the device that we need to restore to.
The target device of the disaster recovery is passed to the barri filedaemon plugin via the plugin options as follows:
In our case this results in:
*restore jobid=1
You have selected the following JobId: 1
Building directory tree for JobId(s) 1 ...
2 files inserted into the tree.
You are now entering file selection mode where you add (mark) and
remove (unmark) files to be restored. No files are initially added, unless
you used the "all" keyword on the command line.
Enter "done" to leave this mode.
cwd is: /
$ mark *
3 files newly marked.
$ done
Bootstrap records written to /var/lib/bareos/bareos-dir.restore.3.bsr
The job will require the following
Volume(s) Storage(s) SD Device(s)
===========================================================================
Full-0001 File FileStorage
Volumes marked with "*" are online.
2 files selected to be restored.
Defined Clients:
1: bareos-fd
2: linuxlive-fd
3: windowsdr-fd
Select the Client (1-3): 2
Using Catalog "MyCatalog"
Run Restore job
JobName: RestoreFiles
Bootstrap: /var/lib/bareos/bareos-dir.restore.3.bsr
Where: /tmp/bareos-restores
Replace: Always
FileSet: LinuxAll
Backup Client: linuxlive-fd
Restore Client: linuxlive-fd
Format: Native
Storage: File
When: 2025-10-02 15:10:49
Catalog: MyCatalog
Priority: 10
Plugin Options: *None*
OK to run? (yes/mod/no): mod
Parameters to modify:
1: Level
2: Storage
3: Job
4: FileSet
5: Restore Client
6: Backup Format
7: When
8: Priority
9: Bootstrap
10: Where
11: File Relocation
12: Replace
13: JobId
14: Plugin Options
Select parameter to modify (1-14): 14
Please enter Plugin Options string: barri:files=/dev/nvme0n1
Run Restore job
JobName: RestoreFiles
Bootstrap: /var/lib/bareos/bareos-dir.restore.3.bsr
Where: /tmp/bareos-restores
Replace: Always
FileSet: LinuxAll
Backup Client: linuxlive-fd
Restore Client: linuxlive-fd
Format: Native
Storage: File
When: 2025-10-02 15:10:49
Catalog: MyCatalog
Priority: 10
Plugin Options: barri:files=/dev/nvme0n1
OK to run? (yes/mod/no): yes
* you have messages
messages
[...] bareos-dir JobId 5: Version: 25.0.0~pre1074.e81033063 (01 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 5: Start Restore Job RestoreFiles.2025-10-02_15.15.46_16
[...] bareos-dir JobId 5: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 5: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 5: Using Device "FileStorage" to read.
[...] bareos-dir JobId 5: Connected Client: linuxlive-fd at linuxlive:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 5: Handshake: Immediate TLS
[...] bareos-dir JobId 5: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 5: Connected File Daemon at linuxlive:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 5: Version: 25.0.0~pre1074.e81033063 (01 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-sd JobId 5: Ready to read from volume "Full-0001" on device "FileStorage" (/var/lib/bareos/storage).
[...] bareos-sd JobId 5: Forward spacing Volume "Full-0001" to file:block 0:223.
[...] localhost-live-fd JobId 5: Version: 25.0.0~pre1077.b73cecf21 (01 October 2025) Fedora 42
[...] localhost-live-fd JobId 5: restore started (file = /tmp/bareos-restores/@BARRI/windr-fd.barri)
[...] localhost-live-fd JobId 5: Restoring 1 Disks
[...] localhost-live-fd JobId 5: Restoring disk 0
[...] localhost-live-fd JobId 5: disk 0 is neither a block device, nor a regular file. Continuing without size check
[...] bareos-sd JobId 5: End of Volume at file 8 on device "FileStorage" (/var/lib/bareos/storage), Volume "Full-0001"
[...] bareos-sd JobId 5: End of all volumes.
[...] bareos-sd JobId 5: Releasing device "FileStorage" (/var/lib/bareos/storage).
[...] localhost-live-fd JobId 5: restore finished
[...] localhost-live-fd JobId 5: starting restore of backup log into debug log (level = 300)
[...] localhost-live-fd JobId 5: restore of backup log is done
[...] localhost-live-fd JobId 5: restore finished
[...] bareos-dir JobId 5: Bareos bareos-dir 25.0.0~pre1074.e81033063 (01Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 5
Job: RestoreFiles.2025-10-02_15.15.46_16
Restore Client: "linuxlive-fd" 25.0.0~pre1077.b73cecf21 (01Oct25) Fedora 42,redhat
Start time: 02-Okt-2025 15:15:48
End time: 02-Okt-2025 15:33:27
Elapsed time: 17 mins 39 secs
Files Expected: 2
Files Restored: 2
Bytes Restored: 102,381,443,939
Rate: 96677,5 KB/s
FD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Restore OK
Restore the .barri image to the filesystem
Additionally to the option to restore the .barri disaster recovery
image via the filedaemon plugin, it is also possible to recover the
.barri image file to the filesystem. This is required to recover a
Windows Computer via the Linux or Windows version of the barri-cli.exe tool.
Recovering the .barri image file to the filesystem is easy.
If the Bareos File Daemon that is selected for the recovery has the barri-fd plugin loaded, you can use the copy= plugin option to save the image to disk.
When recovered to a filedaemon that has not loaded the barri plugin,
the barri image will get restored as normal file in the filesystem.
Just mark the .barri disaster recovery image for recovery
and send the restore to the filedaemon of the bareos server:
*restore jobid=13
You have selected the following JobId: 13
Building directory tree for JobId(s) 13 ...
2 files inserted into the tree.
You are now entering file selection mode where you add (mark) and
remove (unmark) files to be restored. No files are initially added, unless
you used the "all" keyword on the command line.
Enter "done" to leave this mode.
cwd is: /
$ mark *
3 files newly marked.
$ done
Bootstrap records written to /var/lib/bareos/bareos-dir.restore.7.bsr
[...]
2 files selected to be restored.
Defined Clients:
1: bareos-fd
2: linuxlive-fd
3: windowsdr-fd
Select the Client (1-3): 1
Using Catalog "MyCatalog"
Run Restore job
JobName: RestoreFiles
[...]
Plugin Options: *None*
OK to run? (yes/mod/no): yes
[...]
* messages
[...] bareos-dir JobId 14: Version: 25.0.0~pre1074.e81033063 (01 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 14: Start Restore Job RestoreFiles.2025-10-08_09.31.59_10
[...] bareos-dir JobId 14: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 14: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 14: Using Device "FileStorage" to read.
[...] bareos-dir JobId 14: Probing client protocol... (result will be saved until config reload)
[...] bareos-dir JobId 14: Connected Client: bareos-fd at localhost:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 14: Handshake: Immediate TLS
[...] bareos-dir JobId 14: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] barri-server.bareos-fd JobId 14: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] barri-server.bareos-fd JobId 14: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 14: Version: 25.0.0~pre1074.e81033063 (01 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-sd JobId 14: Ready to read from volume "Full-0001" on device "FileStorage" (/var/lib/bareos/storage).
[...] barri-server.bareos-fd JobId 14: Version: 25.0.0~pre1074.e81033063 (01 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-sd JobId 14: Forward spacing Volume "Full-0001" to file:block 0:223.
[...] bareos-sd JobId 14: End of Volume at file 12 on device "FileStorage" (/var/lib/bareos/storage), Volume "Full-0001"
[...] bareos-sd JobId 14: Ready to read from volume "Full-0002" on device "FileStorage" (/var/lib/bareos/storage).
[...] bareos-sd JobId 14: Forward spacing Volume "Full-0002" to file:block 0:223.
[...] bareos-sd JobId 14: End of Volume at file 0 on device "FileStorage" (/var/lib/bareos/storage), Volume "Full-0002"
[...] bareos-sd JobId 14: End of all volumes.
[...] bareos-sd JobId 14: Releasing device "FileStorage" (/var/lib/bareos/storage).
[...] bareos-dir JobId 14: Bareos bareos-dir 25.0.0~pre1074.e81033063 (01Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 14
Job: RestoreFiles.2025-10-08_09.31.59_10
Restore Client: "bareos-fd" 25.0.0~pre1074.e81033063 (01Oct25) AlmaLinux Kitten release 10 (Lion Cub),redhat
Start time: 08-Okt-2025 09:32:01
End time: 08-Okt-2025 09:47:20
Elapsed time: 15 mins 19 secs
Files Expected: 2
Files Restored: 2
Bytes Restored: 133,917,942,676
Rate: 145721,4 KB/s
FD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Restore OK
The file will be restored into the file <where>/@BARRI/winddr-fd.barri.
Restore with the Linux barri-cli commandline tool
The barri-cli linux commandline tool is part of the bareos-filedaemon-barri-plugin package. To be able to use it in a linux live system, you can either install it into the live system, or install it onto another computer and copy the tool into the live system via portable drive.
After installation, the barri-cli is available as /usr/bin/barri-cli.
For the recovery we prepare a USB drive with both the barri-cli binary and the windr-fd.barri disaster recovery
image.
The recovery process is as follows:
Boot the computer to be recovered into a live linux system. In this test we used the Fedora Live Installation System.
Mount the prepared USB drive with barri-cli and the
.barriimage file into the live system.Open a shell with root rights in a terminal and change to the USB Drive mount point. (e.g.
/run/media/liveuser/Barri)Use lsblk to determine the name of the drive(s) that the recovery should overwrite. In our case it is
nvme0n1Call barri-cli to restore the
windr-fd.barrionto the drive.
root@livesystem: ./barri-cli restore --files /dev/nvme0n1 < @BARRI/windr-fd.barri
barri - bareos recovery imager
Version 25.0.0~pre1093.c2d6db38b (06 October 2025)
Copyright (C) 2025-2025 Bareos GmbH & Co. KG
Get professional support from https://www.bareos.com
Restoring 1 Disks
Restoring disk 0
disk 0 is neither a block device, nor a regular file. Continuing without size check
[====> ] 9% [00m:43s<07m:22s] 261.80 MiB/s
As barri-cli reads the image file from standard input (stdin) it is very flexible. If the live linux has network connectivity, the barri file can be piped directly through ssh. Also it is possible to provide the image via http, network drive or any other means that make sense in your environment.
Examples:
ssh root@livesytem barri-cli restore --files /dev/nvme0n1 < /path/to/barri/image.barri
curl --silent http://url/of/the/barri_file.barri | barri-cli restore --files /dev/nvme0n1
Restore with the Windows barri-cli.exe commandline tool
If the linux live system approach is unsuitable, e.g. because the disks are not recognized because of missing drivers, it is possible to use the Windows Version of barri-cli for recovery.
One approch is to connect the disk that needs to be recovered to a second Windows Machine and recover if from there.
The second approach is to prepare a Windows PE live system and add the required drivers so that the Windows live system recognizes the disks on the original hardware.
In any case, make sure that the disk is not in use, as the recovery will fail if the disk is in use by windows.
Preparing barri-cli.exe to be run on an USB Stick
barri-cli.exe depends on the c++ runtime dlls and on zlib1.dll. We suggest to create a folder barri on your USB Stick (F:) and copy the required files into that folder with the following commands:
rem Set your driveletter in the next line
set DRIVE=F:\
set BARRIDIR=%DRIVE%\barri
md %BARRIDIR%
copy "C:\Program Files\Bareos\barri-cli.exe" %BARRIDIR%
copy "C:\Program Files\Bareos\zlib1.dll" %BARRIDIR%
copy "C:\Windows\System32\msvcp140*.dll" %BARRIDIR%
copy "C:\Windows\System32\vcruntime140*.dll" %BARRIDIR%
The resulting directory should look similar to the following:
barri
├── barri-cli.exe
├── msvcp140_1.dll
├── msvcp140_2.dll
├── msvcp140_atomic_wait.dll
├── msvcp140_clr0400.dll
├── msvcp140_codecvt_ids.dll
├── msvcp140.dll
├── vcruntime140_1.dll
├── vcruntime140_clr0400.dll
├── vcruntime140.dll
├── vcruntime140_threads.dll
└── zlib1.dl
Creating a Windows PE image
Please check the Microsoft Documentation for the details. We will only give a short overview of the steps to create a Windows PE Boot Image.
Install the Windows Assessment and Deployment Kit (ADK) deployment tools and the ADK Windows PE Add-ons
Start the “Start the Deployment and Imaging Tools Environment as an administrator” which lies in
C:\Program Files (x86)\Windows Kits\10\Assessment and Deployment Kit\Deployment Tools\DandISetEnv.bat
Change into the Windows PE Directory for amd64:
cd "..\Windows Preinstallation Environment\amd64"
Prepare the Windows PE Working Set:
copype amd64 C:\WinPE_amd64
md C:\WinPE_amd64\mount
Dism /Mount-Image /ImageFile:"en-us\winpe.wim" /index:1 /MountDir:"C:\WinPE_amd64\mount"
Add latest updates to the Image:
Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Users\User\Downloads\windows10.0-kb5065744-x86_b709e76641ebeb7eb36e79dfb9f469b9611a82b8.msu"
Dism /Add-Package /Image:"C:\WinPE_amd64\mount" /PackagePath:"C:\Users\User\Downloads\windows10.0-kb5065755-x86-ndp48_69a8659b2ce13e5d2db14494a95683ef39dd0b42.msu"
Lock in the updates:
md C:\temp
Dism /Cleanup-Image /Image:C:\WinPE_amd64\mount /Startcomponentcleanup /Resetbase /ScratchDir:C:\temp
Unmount the Image
Dism /Unmount-Image /MountDir:"C:\WinPE_amd64\mount" /commit
Write the Windows PE Bootmedium to Drive D:
MakeWinPEMedia /UFD C:\WinPE_amd64 D: /bootex
Note
Installing the Updates was required to successfully boot with Secure Boot enabled in our test environment.
Note
The Windows PE Boot Medium cannot exceed 32GB in size. For Workarounds please see the Microsoft Documentation
Recovery in Windows PE using barri-cli.exe
Now use the just created USB Drive to boot the Computer that you want to restore. After successful bootup the computer show a cmd.exe commandline window like below:
It is now safe to remove the Windows PE USB Disk, and we suggest to do so to reduce the number of disks that are connected to the computer and to also free one additional hardware port.
Now connect the USB Drive to the Windows PE Computer. You can use the commandline tool diskpart to determine both the detected disks and volumes:
X:\Windows\System32>diskpart
Microsoft DiskPart version 10.0.26100.1
Copyright (C) Microsoft Corporation.
On computer: MININT-DE9S2KM
DISKPART>
DISKPART> list disk
Disk ### Status Size Free Dyn Gpt
-------- ------------- ------- ------- --- ---
Disk 0 Online 256 GB 234 GB *
Disk 1 Online 460 GB 1024 KB
Take note what disk number(s) the disks have that you want to recover to. In this example, we want to recover disk 0.
DISKPART> list volume
Volume ### Ltr Label Fs Type Size Status Info
---------- --- ----------- ----- ---------- ------- --------- --------
Volume 0 D CESE_X64FRE UDF CD-ROM 4875 MB Healthy
Volume 1 NTFS Partition 256 GB Healthy
Volume 2 FAT32 Partition 100 MB Healthy Hidden
Volume 3 C Barri NTFS Partition 460 GB Healthy
DISKPART>exit
Now change the directory to the USB drive containing barri-cli.exe
and the .barri image file.
In our case the drive is C:.
To recover a .barri image, we call barri-cli.exe in the following way:
C:\barri\barri-cli.exe --to-disks <disks to write to> < <path_to_barri_file>
Applied to our example this leads to:
C:\barri\barri-cli.exe --to-disks 0 < @BARRI\windr-fd.barri
barri - bareos recovery imager
Version 25.0.0~pre1152.a0abe56e3 (09 October 2025)
Copyright (C) 2025-2025 Bareos GmbH & Co. KG
Get professional support from https://www.bareos.com
found 3 volumes on the selected disks
begin disk { size: 256060514304, extent count: 20582 }
[> ] 0% [00:00s<00:00s]
[=> ] 2% [00m:32s<09m:01s] 120.50 MiB/s
[...]
[=================================================>] 99% [13m:54s<00m:01s] 152.25 MiB/s
disk done
[=================================================>] 99% [13m:55s<00m:01s] 152.25 MiB/s
[==================================================] 100% [13m:56s<00m:00s] Done
Note
If the target disk is not empty it can be required to remove all volumes from the disk using diskpart before barri can recover the image.
When all disks have been recovered, you can unplug all removable drives and close the Windows PE commandline window. The computer will restart and the recovered OS will start.
Description of all Plugin Options
The windows plugin has the following options:
- unknown disks
If this option is given, the barri plugin will also save disks that contain no snapshotted data. This could be a linux disk in a multi-boot environment.
- unknown partitions
If this option is given, the barri plugin will also save partitions that contain no snapshotted data. This could be a linux partition in a multi-boot environment.
- unknown extents
If this option is given, the barri plugin will save extents that contain no snapshotted data. This usually does not make sense, as it will enlarge the backup size with unneeded data.
- ignore disks=<disks to ignore>
If this option is given, the barri plugin will skip the disks with the given numbers. To avoid disk 1 being snapshotted and backed up, add ignore disks=1 to the plugin options
The linux plugin has the following options:
- files=<list of file paths> [*]
If this option is set to a comma-separated list of files, then bareos will restore the disks to the given files. The first disk from the image will get restored to the first given file, the second disk will get restored to the second file, and so on. If the number of files and disks do not match up, then the restore will fail.
- directory=<path to directory> [*]
If this option is set to a directory path, then bareos will restore all disks as newly created files in that directory.
- copy=<path to a file> [*]
If this option is set to a file, then bareos will write a copy the image to that file. This copy can then be restored manually using barri-cli.
Note
Only a single option marked [*] may be given during a single restore.
bpipe Plugin
The bpipe plugin is a generic pipe program, that simply transmits the data from a specified program to Bareos for backup, and from Bareos to a specified program for restore. The purpose of the plugin is to provide an interface to any system program for backup and restore. That allows you, for example, to do database backups without a local dump. By using different command lines to bpipe, you can backup any kind of data (ASCII or binary) depending on the program called.
On Linux, the Bareos bpipe plugin is part of the bareos-filedaemon package and is therefore installed on any system running the filedaemon.
The bpipe plugin is so simple and flexible, you may call it the “Swiss Army Knife” of the current existing plugins for Bareos.
The bpipe plugin is specified in the Include section of your Job’s FileSet resource.
The syntax and semantics of the Plugin directive require the first part of the string up to the colon to be the name of the plugin. Everything after the first colon is ignored by the File daemon but is passed to the plugin. Thus the plugin writer may define the meaning of the rest of the string as he wishes. The full syntax of the plugin directive as interpreted by the bpipe plugin is:
Since Bareos Version >= 20 the plugin string can be spread over multiple lines using quotes as shown above.
- plugin
is the name of the plugin with the trailing -fd.so stripped off, so in this case, we would put bpipe in the field.
- filepath
specifies the namespace, which for bpipe is the pseudo path and filename under which the backup will be saved. This pseudo path and filename will be seen by the user in the restore file tree. For example, if the value is /MySQL/mydump.sql, the data backed up by the plugin will be put under that “pseudo” path and filename. You must be careful to choose a naming convention that is unique to avoid a conflict with a path and filename that actually exists on your system.
- readprogram
for the bpipe plugin specifies the “reader” program that is called by the plugin during backup to read the data. bpipe will call this program by doing a popen on it.
- writeprogram
for the bpipe plugin specifies the “writer” program that is called by the plugin during restore to write the data back to the filesystem. To simply create a file, containing the data of the backup, following command can by used on a Unix system:
writer=sh -c 'cat >/var/tmp/bpipe.data'
Please note that the two items above describing the “reader” and “writer”, these programs are “executed” by Bareos, which means there is no shell interpretation of any command line arguments you might use. If you want to use shell characters (redirection of input or output, …), then we recommend that you put your command or commands in a shell script and execute the script. In addition if you backup a file with reader program, when running the writer program during the restore, Bareos will not automatically create the path to the file. Either the path must exist, or you must explicitly do so with your command or in a shell script.
See the examples about Backup of a PostgreSQL Database and Backup of a MySQL Database.
Environment variables
For both the readprogram and the writeprogram, the following environment variables are being set:
BareosClientName |
Client name of the current job |
BareosJobId |
Job id of the current job |
BareosJobLevel |
Job level of the current job |
BareosSinceTime |
Since time of the differential/incremental backup |
BareosJobType |
Job type of the current job |
The BareosSinceTime is 0 during full backups and restores. The BareosjobLevel is the space character (” “) during restores.
GlusterFS Plugin
Deprecated since version 25.0.0.
Opposite to the GFAPI Backend that is used to store data on a Gluster system, this plugin is intended to backup data from a Gluster system to other media. The package bareos-filedaemon-glusterfs-plugin (Version >= 15.2.0) contains an example configuration file, that must be adapted to your environment.
Grpc Plugin
The grpc plugin is a plugin that allows you to run a separate executable as a bareos plugin. This executable talks to the core via grpc remote procedure calls.
This has multiple upsides for users, such as:
A crash inside a plugin will not also crash the daemon
It eliminates some classes of concurrency problems related to the use of global state inside plugins
This plugin on its own is not very useful. Its only a bridge between the bareos core and the actual plugin doing the work.
The plugin comes with two executables, grpc-test-module and bareos-grpc-fd-plugin-bridge, which allow you to make use of this bridge. As the name suggests, grpc-test-module is a simple module that can be used to test that the bridge is working. bareos-grpc-fd-plugin-bridge on the other hand is a handy little executable that can be used to load and run normal bareos plugins (including python plugins) in a separate process.
Status of the Grpc Plugin
This plugin is still in an experimental phase. The API between core and plugins may change at any time.
Installation of the Grpc Plugin
The grpc plugin, together with the grpc-test-module and bareos-grpc-fd-plugin-bridge, can be installed with the bareos-filedaemon-gprc-plugin package.
Configuration of the Grpc Plugin
The Grpc Plugin receives as first argument the name of the executable that it should execute. This executable is assumed to be in the normal bareos plugin directory.
Grpc Fd Plugin Bridge Module
The Grpc Fd Plugin Bridge is a grpc module that can be used to start any File Daemon Plugins in a separate process. This is especially useful when used with the python-fd Plugin as this ensures that no state is shared between different jobs.
a quick overview of the architecture
This plugin does not take any options, but expects its arguments to be a valid bareos plugin definition.
Example
This fileset will call the python-fd plugin pyplug with the argument arg1=val1 in a separate process.
Note
We recommend using Grpc Fallback instead of explicitly using the grpc plugin if you plan on using the Grpc Fd Plugin Bridge Module.
Grpc Fallback
If you want to use the grpc plugin to start normal bareos plugins via the Grpc Fd Plugin Bridge Module in a separate process, then we recommend you to use grpc fallback. In this mode regular plugin directives in your fileset get sent to the grpc plugin _if_ the specified plugin was not loaded. E.g. if your filedaemon does not load the python-fd Plugin and you try to backup a fileset including a python plugin directive, then the grpc plugin is asked to take care of it.
The grpc fallback mode is enabled if you dont unset Grpc Module (Fd->Client)
and load the Grpc Plugin in the fd.
Example (Fallback)
When we now start a backup with the Python fileset on the client fallback-fd, then the file daemon will automatically use the grpc plugin and the Grpc Fd Plugin Bridge Module to try and load python-fd.so and run the backup in a separate process.
This backup will count as a backup done with the python plugin itself, so it can be restored even on clients which only have access to the python plugin. This also happens completely transparently to the director, so it will happily continue the current backup chain, i.e. it will not force trigger a full backup.
You can verify that the grpc fallback was indeed chosen by looking into the joblog:
[...]
fallback-fd JobId 1: selected inferior: python3
fallback-fd JobId 1: loaded inferior: Python File Daemon Plugin
Version: 4 (May 2020)
Author: Bareos GmbH & Co. KG
License: Bareos AGPLv3
fallback-fd JobId 1: loaded inferior successfully
[...]
Hyper-V Plugin
The Hyper-V Plugin allows you to backup hyper-v virtual machines. It makes use of RCT (Resilient Change Tracking) Technology to make extremely fast incremental backups.
Limitation: Local Paths
Currently only disks with a local path can be backed up.
Limitation: Currently .vhds disks are unsupported
Currently .vhds disks are unsupported; only .vhdx and .vhd disks are supported.
Requirements
The Hyper-V plugin needs to be installed on a Windows Computer with the Hyper-V Windows feature installed and running.
Installation
To install the Hyper-V plugin use run the Bareos Windows installer and install the File Daemon and the Hyper-V File Daemon Plugin.
Configuration
The Hyper-V Plugin expects the Name of the Virtual Machine to be backed up as plugin parameter vmname.
Make sure to add or enable the following settings in your Bareos File Daemon configuration and restart the Bareos File Daemon service.
To verify that the plugin was loaded, execute status client and look for the Hyper-V plugin information:
*status client=hyperv-fd
Connecting to Client hyperv-fd at hyperv:9102
[...]
hypev-fd Version: 25.0.0~pre925.de8540c15 (20 October 2025) VSS Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit
Daemon started 20-Okt-25 14:56. Jobs: run=0 running=0, self-compiled binary
Sizeof: boffset_t=8 size_t=8 debug=0 trace=0 bwlimit=0kB/s
Plugin Info:
Plugin : hyper-v-fd.dll
Description: Bareos Hyper-V Windows File Daemon Plugin
Version : 1 (April 2025)
Author : Sebastian Sura
License : Bareos AGPLv3
Usage :
hyper-v:config_file=<path>:vmname=<name>
[...]
The next step is to configure a fileset for each VM to be backed up. In our case the VM Name is Alma10:
Limitation: Unique VM Name is required
The name of the Virtual Machine needs to be unique. If multiple VMs with the same name exist, the backup will be cancelled.
Note
Currently the plugin does not support sparse full backups. That means that the full dynamic disk is backed up even if only a small part of it is actually used. For this reason we recommend using compression in hyper-v filesets, as this will allow the backed up data to be shrunk again to their sparse size.
All parameters can optionally also be given inside a json configuration file. You can specify the configuration file to use via the config_file option.
{
"vmname" : "My Virtual Machine"
}
You can freely mix a config_file with other parameters specified directly in the fileset. Parameters from the fileset always take precedence.
Backup
To create a backup of your virtual machine, just run the job hyper-v-alma10 from the bconsole with the Backup Level Full.
The Bareos Plugin will create a checkpoint and backup the virtual machine:
run job=hyper-v-alma10 level=Full yes
[...] bareos-dir JobId 118: Version: 25.0.0~pre1093.c2d6db38b (06 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 118: Start Backup JobId 118, Job=hyper-v-alma10.2025-10-23_15.46.41_08
[...] bareos-dir JobId 118: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 118: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 118: Connected Client: hyperv-fd at hyperv:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 118: Handshake: Immediate TLS
[...] bareos-dir JobId 118: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] hyperv-fd JobId 118: Successfully connected to 'ROOT\VIRTUALIZATION\V2'
[...] bareos-sd JobId 118: Using just in time reservation for job 118
[...] bareos-dir JobId 118: Using Device "JustInTime Device" to write.
[...] bareos-sd JobId 118: Connected File Daemon at hyperv:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 118: Version: 25.0.0~pre1093.c2d6db38b (06 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] hyperv-fd JobId 118: Fileset has no "File=" directives, ignoring FilesNotToBackup Registry key
[...] hyperv-fd JobId 118: Version: 25.0.0~pre965.f8bad1c5a (23 October 2025) Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit
[...] hyperv-fd JobId 118: preparing backup of VM 'Alma10'
[...] hyperv-fd JobId 118: creating snapshot of VM 'Alma10' ...
[...] hyperv-fd JobId 118: created snapshot with name 'Bareos JobId 118'
[...] hyperv-fd JobId 118: exporting system definition for VM 'Alma10' to C:\WINDOWS\TEMP\Bareos-118
[...] hyperv-fd JobId 118: retrieving information from snapshot ...
[...] hyperv-fd JobId 118: finished preparing backup
[...] hyperv-fd JobId 118: Starting backup of metadata C:\WINDOWS\TEMP\Bareos-118\Virtual Machines\7802CE25-83F1-48E0-9637-941262284282.VMRS
[...] hyperv-fd JobId 118: Starting backup of metadata C:\WINDOWS\TEMP\Bareos-118\Virtual Machines\7802CE25-83F1-48E0-9637-941262284282.vmgs
[...] bareos-sd JobId 118: JustInTime Reservation: Finding drive to reserve.
[...] bareos-dir JobId 118: Created new Volume "Full-0008" in catalog.
[...] hyperv-fd JobId 118: Starting backup of metadata C:\WINDOWS\TEMP\Bareos-118\Virtual Machines\7802CE25-83F1-48E0-9637-941262284282.vmcx
[...] bareos-sd JobId 118: Using Device "File0001" (/var/lib/bareos/storage) to write.
[...] hyperv-fd JobId 118: Starting backup of disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{76F49D96-6EB4-441E-A406-B9C47E0523F5}_D08F5D3B-71D8-4C1D-8909-EECDD1675E76.avhdx'
[...] hyperv-fd JobId 118: Backing up disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{76F49D96-6EB4-441E-A406-B9C47E0523F5}_D08F5D3B-71D8-4C1D-8909-EECDD1675E76.avhdx' as '{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx'
[...] bareos-sd JobId 118: Labeled new Volume "Full-0008" on device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 118: Moving to end of data on volume "Full-0008"
[...] bareos-sd JobId 118: Ready to append to end of Volume "Full-0008" size=223
[...] bareos-dir JobId 118: Max Volume jobs=1 exceeded. Marking Volume "Full-0008" as Used.
[...] hyperv-fd JobId 118: Starting backup of disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{6882FDF0-4924-4CFD-96CE-096235890E15}_0706D94C-D2FA-4F17-89CC-869ECC021208.avhdx'
[...] hyperv-fd JobId 118: Backing up disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{6882FDF0-4924-4CFD-96CE-096235890E15}_0706D94C-D2FA-4F17-89CC-869ECC021208.avhdx' as '{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx'
[...] bareos-sd JobId 118: Releasing device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 118: Elapsed time=00:01:31, Transfer rate=44.68 M Bytes/second
[...] bareos-dir JobId 118: Insert of attributes batch table with 5 entries start
[...] bareos-dir JobId 118: Insert of attributes batch table done
[...] bareos-dir JobId 118: Bareos bareos-dir 25.0.0~pre1093.c2d6db38b (06Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 118
Job: hyper-v-alma10.[...]_08
Backup Level: Full
Client: "hyperv-fd" 25.0.0~pre965.f8bad1c5a (23Oct25) Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit,Windows-x64
FileSet: "hyperv-alma10" [...]
Pool: "Full" (From Job FullPool override)
Catalog: "MyCatalog" (From Client resource)
Storage: "File" (From Job resource)
Scheduled time: 23-Okt-2025 15:46:41
Start time: 23-Okt-2025 15:46:43
End time: 23-Okt-2025 15:48:16
Elapsed time: 1 min 33 secs
Priority: 10
Allow Mixed Priority: no
FD Files Written: 9
SD Files Written: 9
FD Bytes Written: 4,066,217,365 (4.066 GB)
SD Bytes Written: 4,066,219,893 (4.066 GB)
Rate: 43722,8 KB/s
Software Compression: 65,6 % (lz4)
VSS: no
Encryption: no
Accurate: no
Volume name(s): Full-0008
Volume Session Id: 3
Volume Session Time: 1761227133
Last Volume Bytes: 4,066,901,446 (4.066 GB)
Non-fatal FD errors: 0
SD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Backup OK
Now we let the VM run a bit which will alter the VM Disk contents. The data being saved in the following incremental backup depends on the amount of disk data that has been changed since the last backup. The next step is to run an incremental backup of the VM:
*run job=hyper-v-alma10 level=Incremental yes
[...] bareos-dir JobId 123: Version: 25.0.0~pre1093.c2d6db38b (06 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 123: Start Backup JobId 123, Job=hyper-v-alma10.2025-10-23_15.58.18_18
[...] bareos-dir JobId 123: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 123: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 123: Connected Client: hyperv-fd at hyperv:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 123: Handshake: Immediate TLS
[...] bareos-dir JobId 123: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] hyperv-fd JobId 123: Successfully connected to 'ROOT\VIRTUALIZATION\V2'
[...] bareos-sd JobId 123: Using just in time reservation for job 123
[...] bareos-dir JobId 123: Using Device "JustInTime Device" to write.
[...] bareos-sd JobId 123: Connected File Daemon at hyperv:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 123: Version: 25.0.0~pre1093.c2d6db38b (06 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] hyperv-fd JobId 123: Fileset has no "File=" directives, ignoring FilesNotToBackup Registry key
[...] hyperv-fd JobId 123: Version: 25.0.0~pre965.f8bad1c5a (23 October 2025) Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit
[...] hyperv-fd JobId 123: preparing backup of VM 'Alma10'
[...] hyperv-fd JobId 123: creating snapshot of VM 'Alma10' ...
[...] hyperv-fd JobId 123: created snapshot with name 'Bareos JobId 123'
[...] hyperv-fd JobId 123: exporting system definition for VM 'Alma10' to C:\WINDOWS\TEMP\Bareos-123
[...] hyperv-fd JobId 123: retrieving information from snapshot ...
[...] hyperv-fd JobId 123: finished preparing backup
[...] hyperv-fd JobId 123: Starting backup of metadata C:\WINDOWS\TEMP\Bareos-123\Virtual Machines\7802CE25-83F1-48E0-9637-941262284282.VMRS
[...] bareos-sd JobId 123: JustInTime Reservation: Finding drive to reserve.
[...] bareos-dir JobId 123: Created new Volume "Incremental-0010" in catalog.
[...] hyperv-fd JobId 123: Starting backup of metadata C:\WINDOWS\TEMP\Bareos-123\Virtual Machines\7802CE25-83F1-48E0-9637-941262284282.vmgs
[...] hyperv-fd JobId 123: Starting backup of metadata C:\WINDOWS\TEMP\Bareos-123\Virtual Machines\7802CE25-83F1-48E0-9637-941262284282.vmcx
[...] bareos-sd JobId 123: Using Device "File0001" (/var/lib/bareos/storage) to write.
[...] hyperv-fd JobId 123: Starting backup of disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{76F49D96-6EB4-441E-A406-B9C47E0523F5}.vhdx'
[...] hyperv-fd JobId 123: Backing up disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{76F49D96-6EB4-441E-A406-B9C47E0523F5}.vhdx' as '{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx'
[...] hyperv-fd JobId 123: Starting backup of disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{6882FDF0-4924-4CFD-96CE-096235890E15}.vhdx'
[...] hyperv-fd JobId 123: Backing up disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{6882FDF0-4924-4CFD-96CE-096235890E15}.vhdx' as '{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx'
[...] bareos-sd JobId 123: Labeled new Volume "Incremental-0010" on device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 123: Moving to end of data on volume "Incremental-0010"
[...] bareos-sd JobId 123: Ready to append to end of Volume "Incremental-0010" size=237
[...] bareos-dir JobId 123: Max Volume jobs=1 exceeded. Marking Volume "Incremental-0010" as Used.
[...] bareos-sd JobId 123: Releasing device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 123: Elapsed time=00:00:06, Transfer rate=438.9 K Bytes/second
[...] bareos-dir JobId 123: Insert of attributes batch table with 5 entries start
[...] bareos-dir JobId 123: Insert of attributes batch table done
[...] bareos-dir JobId 123: Bareos bareos-dir 25.0.0~pre1093.c2d6db38b (06Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 123
Job: hyper-v-alma10.2025-10-23_15.58.18_18
Backup Level: Incremental, since=2025-10-23 15:46:43
Client: "hyperv-fd" 25.0.0~pre965.f8bad1c5a (23Oct25) Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit,Windows-x64
FileSet: "hyperv-alma10" 2025-10-21 15:03:45
Pool: "Incremental" (From Job IncPool override)
Catalog: "MyCatalog" (From Client resource)
Storage: "File" (From Job resource)
Scheduled time: 23-Okt-2025 15:58:18
Start time: 23-Okt-2025 15:58:20
End time: 23-Okt-2025 15:58:28
Elapsed time: 8 secs
Priority: 10
Allow Mixed Priority: no
FD Files Written: 9
SD Files Written: 9
FD Bytes Written: 2,631,072 (2.631 MB)
SD Bytes Written: 2,633,524 (2.633 MB)
Rate: 328,9 KB/s
Software Compression: 88,2 % (lz4)
VSS: no
Encryption: no
Accurate: no
Volume name(s): Incremental-0010
Volume Session Id: 7
Volume Session Time: 1761227133
Last Volume Bytes: 2,646,849 (2.646 MB)
Non-fatal FD errors: 0
SD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Backup OK
We now have a full Backup of the VM and also an incremental Backup that only contains the changed blocks of the virtual disks.
Restore
The next step is to restore the Virtual Machine. Therefore run the restore command and mark all files that are available for restore:
*restore client=hyperv-fd fileset=hyperv-alma10
First you select one or more JobIds that contain files
[...]
5: Select the most recent backup for a client
[...]
Select item: (1-13): 5
+-------+-------+----------+---------------+---------------------+------------------+
| jobid | level | jobfiles | jobbytes | starttime | volumename |
+-------+-------+----------+---------------+---------------------+------------------+
| 105 | F | 9 | 4,066,290,590 | 2025-10-22 14:54:38 | Full-0003 |
| 106 | I | 9 | 741,463 | 2025-10-22 15:17:46 | Incremental-0005 |
+-------+-------+----------+---------------+---------------------+------------------+
You have selected the following JobIds: 105,106
Building directory tree for JobId(s) 105,106 ...
7 files inserted into the tree.
You are now entering file selection mode where you add (mark) and
remove (unmark) files to be restored. No files are initially added, unless
you used the "all" keyword on the command line.
Enter "done" to leave this mode.
cwd is: /
$ mark *
6 files newly marked.
$ done
Bootstrap records written to /var/lib/bareos/bareos-dir.restore.1.bsr
[...]
Using Catalog "MyCatalog"
Run Restore job
JobName: RestoreFiles
Bootstrap: /var/lib/bareos/bareos-dir.restore.1.bsr
Where: /tmp/bareos-restores
Replace: Always
FileSet: LinuxAll
Backup Client: hyperv-fd
Restore Client: hyperv-fd
Format: Native
Storage: File
When: 2025-10-23 09:15:03
Catalog: MyCatalog
Priority: 10
Plugin Options: *None*
OK to run? (yes/mod/no): yes
[...] bareos-dir JobId 124: Version: 25.0.0~pre1093.c2d6db38b (06 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 124: Start Restore Job RestoreFiles.2025-10-23_16.06.06_21
[...] bareos-dir JobId 124: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 124: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 124: Using Device "File0001" to read.
[...] bareos-dir JobId 124: Connected Client: hyperv-fd at hyperv:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 124: Handshake: Immediate TLS
[...] bareos-dir JobId 124: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] hyperv-fd JobId 124: Successfully connected to 'ROOT\VIRTUALIZATION\V2'
[...] bareos-sd JobId 124: Connected File Daemon at hyperv:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 124: Version: 25.0.0~pre1093.c2d6db38b (06 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-sd JobId 124: Ready to read from volume "Full-0008" on device "File0001" (/var/lib/bareos/storage).
[...] hyperv-fd JobId 124: using 'C:\WINDOWS\TEMP\Bareos-124' as temporary hyper-v import directory
[...] hyperv-fd JobId 124: Version: 25.0.0~pre965.f8bad1c5a (23 October 2025) Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit
[...] bareos-sd JobId 124: Forward spacing Volume "Full-0008" to file:block 0:223.
[...] hyperv-fd JobId 124: restoring disk {AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx ('@HYPER-V/Alma10/disks/{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx') to 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx'
[...] hyperv-fd JobId 124: restoring disk {E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx ('@HYPER-V/Alma10/disks/{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx') to 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx'
[...] bareos-sd JobId 124: End of Volume at file 0 on device "File0001" (/var/lib/bareos/storage), Volume "Full-0008"
[...] bareos-sd JobId 124: Ready to read from volume "Incremental-0010" on device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 124: Forward spacing Volume "Incremental-0010" to file:block 0:237.
[...] bareos-sd JobId 124: Releasing device "File0001" (/var/lib/bareos/storage).
[...] hyperv-fd JobId 124: restoring metadata file '@HYPER-V/Alma10/config/7802CE25-83F1-48E0-9637-941262284282.VMRS' as 'C:\WINDOWS\TEMP\Bareos-124\Alma10\config\7802CE25-83F1-48E0-9637-941262284282.VMRS'
[...] hyperv-fd JobId 124: restoring metadata file '@HYPER-V/Alma10/config/7802CE25-83F1-48E0-9637-941262284282.vmgs' as 'C:\WINDOWS\TEMP\Bareos-124\Alma10\config\7802CE25-83F1-48E0-9637-941262284282.vmgs'
[...] hyperv-fd JobId 124: restoring metadata file '@HYPER-V/Alma10/config/7802CE25-83F1-48E0-9637-941262284282.vmcx' as 'C:\WINDOWS\TEMP\Bareos-124\Alma10\config\7802CE25-83F1-48E0-9637-941262284282.vmcx'
[...] hyperv-fd JobId 124: restoring incremental image of '{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx' (level 1) to 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx'
[...] hyperv-fd JobId 124: restoring incremental image of '{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx' (level 1) to 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx'
[...] hyperv-fd JobId 124: creating a new vm from the restored configuration file 'C:\WINDOWS\TEMP\Bareos-124\Alma10\config\7802CE25-83F1-48E0-9637-941262284282.vmcx'
[...] hyperv-fd JobId 124: updating the configuration of the created vm
[...] hyperv-fd JobId 124: - changing disk path 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{6882FDF0-4924-4CFD-96CE-096235890E15}.vhdx' to restored disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx'
[...] hyperv-fd JobId 124: - changing disk path 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\{76F49D96-6EB4-441E-A406-B9C47E0523F5}.vhdx' to restored disk 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx'
[...] hyperv-fd JobId 124: validating created vm
[...] hyperv-fd JobId 124: realizing created vm
[...] bareos-dir JobId 124: Bareos bareos-dir 25.0.0~pre1093.c2d6db38b (06Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 124
Job: RestoreFiles.2025-10-23_16.06.06_21
Restore Client: "hyperv-fd" 25.0.0~pre965.f8bad1c5a (23Oct25) Microsoft Windows Server 2012 Standard Edition (build 9200), 64-bit,Windows-x64
Start time: 23-Okt-2025 16:06:08
End time: 23-Okt-2025 16:07:56
Elapsed time: 1 min 48 secs
Files Expected: 7
Files Restored: 7
Bytes Restored: 11,833,549,454
Rate: 109569,9 KB/s
FD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Restore OK
After the successful restore, the Virtual Machine shows up in the Hyper-V Manager and can be started.
During recovery, the Hyper-V plugin tries to recover the virtual harddisks to the original place.
In case a harddisk with the same name already exists (usually because the original VM still exists), the plugin will alter the harddisks’ filename with a prefix and store it into the original folder.
The restore job’s termination will be Restore OK – with warnings
[...] hyperv-fd JobId 125: Warning: 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx' already exists,⤶
using 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\bareos-125-0-{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx' for restore instead
[...] hyperv-fd JobId 125: restoring disk {AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx ('@HYPER-V/Alma10/disks/{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx') to⤶
'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\bareos-125-0-{AEE72202-4637-4C3C-8A3A-03806C36F641}.vhdx'
[...] hyperv-fd JobId 125: Warning: 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx' already exists,⤶
using 'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\bareos-125-0-{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx' for restore instead
[...] hyperv-fd JobId 125: restoring disk {E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx ('@HYPER-V/Alma10/disks/{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx') to⤶
'C:\ProgramData\Microsoft\Windows\Virtual Hard Disks\\bareos-125-0-{E4289419-1C8F-4D6E-A195-1BC59C6443EA}.vhdx'
[...] bareos-dir JobId 125: Bareos bareos-dir 25.0.0~pre1093.c2d6db38b (06Oct25):
[...]
FD termination status: OK -- with warnings
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Restore OK -- with warnings
Warning
The restored vm needs a new full backup before continuing with a new incremental backup.
Otherwise the next job will finish in Error:
Fatal error: Cannot continue with hyper-v-alma10. No full backup was found.
Description of all Plugin Options
- config_file (optional)
Path to a json file containing values to use for the other options.
- vmname (mandatory)
Name of the VM
LDAP Plugin
This plugin is intended to backup (and restore) the contents of a LDAP server. It uses normal LDAP operation for this. The package bareos-filedaemon-ldap-python-plugin (Version >= 15.2.0) contains an example configuration file, that must be adapted to your environment.
Please note that the plugin was tested against an OpenLDAP server. Other LDAP servers may behave differently and there might be problems when backing up or restoring objects. Most notably, it will not be possible to restore objects to an Active Directory server.
On restore, if the object to be restored already exists on the LDAP server, it will be deleted first, then restored from the backup. This could cause problems if your LDAP server uses referential integrity (e.g. if a user object is restored, the LDAP server might remove the user from all groups when it is being deleted and recreated during the restore process).
MariaDB mariabackup Plugin
This plugin uses the tool mariabackup to make full and incremental backups of MariaDB databases. mariabackup is part of the standard mariadb installation.
Documentation of mariadb-backup is available online: https://mariadb.com/docs/server/server-usage/backup-and-restore/mariadb-backup.
It is stable since MariaDB 10.1.48
Prerequisites of mariabackup Plugin
The mariabackup binary needs to be installed on the Bareos File Daemon. refer to previous documentation link.
For authentication the .mycnf file of the user running the Bareos File Daemon is used. Before proceeding, make sure that mariabackup can connect to the database, create backups and is able to restore.
Installation of mariabackup Plugin
Make sure you have met the prerequisites, then install the package bareos-filedaemon-mariabackup-python-plugin.
Configuration of mariabackup Plugin
Activate your plugin directory in the Bareos File Daemon configuration. See File Daemon Plugins for more about plugins in general.
Now include the plugin as command-plugin in the Fileset resource:
The plugin will call mariabackup to create a backup stream of all databases in the xbstream format. This stream will be processed by Bareos. Full backups can be made for all table formats, while incremental backups are only supported for InnoDB tables. Incremental backups for other table formats will create a full backup.
You can append options to the plugin call as key=value pairs, separated by ’:’. The following options are available:
With mycnf you can make mariabackup use a special mycnf-file with login credentials.
dumpbinary lets you modify the default command mariabackup.
dumpoptions to modify the options for mariabackup. Default setting is: --backup --stream=xbstream --extra-lsndir=/tmp/individual_tempdir
restorecommand to modify the command for restore. Default setting is: mbstream -x -C
strictIncremental: By default (false), an incremental backup will create data even if the Log Sequence Number (LSN) was not increased since last backup. This is to ensure that eventual changes to MYISAM/ARIA/Rocks tables get into the backup. MYISAM/ARIA/Rocks does not support incremental backups, you will always get a full backup of these tables. If set to true, no data will be written into backup, if the LSN was not changed.
Restore with mariabackup Plugin
With the usual Bareos restore mechanism a file-hierarchy will be created on the restore client under the default restore location:
/tmp/bareos-restores/_mariabackup/
Each restore job gets an own sub-directory named by its jobid, because mariabackup expects an empty directory. In that sub-directory, a new directory is created for every backup job that was part of the Full-Incremental sequence.
The naming scheme is: fromLSN_toLSN_jobid
Example:
/tmp/bareos-restores/_mariabackup/656/
|-- 00000000000000000000_00000000000010129154_0000000604
|-- 00000000000010129154_00000000000010142295_0000000635
|-- 00000000000010142295_00000000000010201260_0000000708
This example shows the restore tree for restore job with ID 656. First sub-directory has all files from the first full backup job with ID 604. It starts at LSN 0 and goes until LSN 10129154.
Next line is the first incremental job with ID 635, starting at LSN 10129154 until 10142295. The third line is the 2nd incremental job with ID 708.
To further prepare the restored files, use the mariabackup --prepare command. Read https://mariadb.com/docs/server/server-usage/backup-and-restore/mariadb-backup/incremental-backup-and-restore-with-mariadb-backup for more information.
Also our systemtest can serve as example see systemtests/tests/py2plug-fd-mariabackup/testrunner
Troubleshooting
If things don’t work as expected, make sure that
the Bareos File Daemon (FD) works in general, so that you can make simple file backups and restores.
the Bareos FD Python plugins work in general, try one of the shipped simple sample plugins.
mariabackup works as user root, MariaDB access needs to be configured properly.
MSSQL Plugin
See chapter Backup of MSSQL Databases with Bareos Plugin.
MySQL Plugin
See the chapters Percona XtraBackup Plugin and Backup of MySQL Databases using the Python MySQL plugin.
Percona XtraBackup Plugin
This plugin uses Perconas XtraBackup tool, to make full and incremental backups of MySQL databases.
The key features of XtraBackup are:
Incremental backups
Backups that complete quickly and reliably
Uninterrupted transaction processing during backups
Savings on disk space and network bandwidth
Higher uptime due to faster restore time
Incremental backups only work for INNODB tables, when using MYISAM, only full backups can be created.
Warning
In MariaDB 10.1 and later, mariabackup is the recommended backup method to use instead of Percona XtraBackup. As such we recommend to use the dedicated plugin for MariaDB.
Prerequisites of percona XtraBackup Plugin
Install the XtraBackup tool from Percona. Documentation and packages are available here: https://www.percona.com/mysql/software. The plugin was successfully tested with XtraBackup versions 2.3.5 and 2.4.4.
For authentication the .mycnf file of the user running the Bareos File Daemon is used. Before proceeding, make sure that XtraBackup can connect to the database and create backups.
Installation of percona XtraBackup Plugin
Make sure you have met the prerequisites, after that install the package bareos-filedaemon-percona-xtrabackup-python-plugin.
Configuration of percona XtraBackup Plugin
Activate your plugin directory in the Bareos File Daemon configuration. See File Daemon Plugins for more about plugins in general.
Now include the plugin as command-plugin in the Fileset resource:
If used this way, the plugin will call XtraBackup to create a backup of all databases in the xbstream format. This stream will be processed by Bareos. If job level is incremental, XtraBackup will perform an incremental backup since the last backup – for InnoDB tables. If you have MyISAM tables, you will get a full backup of those.
You can append options to the plugin call as key=value pairs, separated by ’:’. The following options are available:
With mycnf you can make XtraBackup use a special mycnf-file with login credentials.
dumpbinary lets you modify the default command XtraBackup.
dumpoptions to modify the options for XtraBackup. Default setting is: --backup --datadir=/var/lib/mysql/ --stream=xbstream --extra-lsndir=/tmp/individual_tempdir
restorecommand to modify the command for restore. Default setting is: xbstream -x -C
strictIncremental: By default (false), an incremental backup will create data, even if the Log Sequence Number (LSN) was not increased since last backup. This is to ensure, that eventual changes to MYISAM tables get into the backup. MYISAM does not support incremental backups, you will always get a full backup of these tables. If set to true, no data will be written into backup, if the LSN was not changed.
Restore with percona XtraBackup Plugin
With the usual Bareos restore mechanism a file-hierarchy will be created on the restore client under the default restore location:
/tmp/bareos-restores/_percona/
Each restore job gets an own subdirectory, because Percona expects an empty directory. In that subdirectory, a new directory is created for every backup job that was part of the Full-Incremental sequence.
The naming scheme is: fromLSN_toLSN_jobid
Example:
/tmp/bareos-restores/_percona/351/
|-- 00000000000000000000_00000000000010129154_0000000334
|-- 00000000000010129154_00000000000010142295_0000000335
|-- 00000000000010142295_00000000000010201260_0000000338
This example shows the restore tree for restore job with ID 351. First subdirectory has all files from the first full backup job with ID 334. It starts at LSN 0 and goes until LSN 10129154.
Next line is the first incremental job with ID 335, starting at LSN 10129154 until 10142295. The third line is the 2nd incremental job with ID 338.
To further prepare the restored files, use the XtraBackup --prepare command. For more information read https://docs.percona.com/percona-xtrabackup/2.4/backup_scenarios/incremental_backup.html.
Troubleshooting
If things don’t work as expected, make sure that
the Bareos File Daemon (FD) works in general, so that you can make simple file backups and restores.
the Bareos FD Python plugins work in general, try one of the shipped simple sample plugins.
XtraBackup works as user root, MySQL access needs to be configured properly.
PostgreSQL Plugin
The PostgreSQL plugin supports an online (Hot) backup of database files and database transaction logs (WAL). With online database and transaction logs, the backup plugin can perform Point-In-Time-Restore (PITR) up to a single selected transaction or date/time.
This plugin uses the standard API PostgreSQL backup routines based on pg_backup_start() and pg_backup_stop() functions in non-exclusive mode. (Before PostgreSQL 15 formally pg_start_backup() and pg_stop_backup())
The key features are:
Full and Incremental backups
Point in time recovery
Backups that complete quickly and reliably
Uninterrupted transaction processing during backups
Savings on disk space and network bandwidth
Higher uptime due to faster restore time
Concept
Please make sure to read the PostgreSQL documentation about the backup and restore process: https://www.postgresql.org/docs/current/continuous-archiving.html
This is just a short outline of the tasks performed by the plugin.
Notify PostgreSQL that we want to start backup the database files using the SELECT pg_backup_start() statement
Backup database files
Detect if tablespace are in use. Backup the external locations of all tablespaces.
Notify PostgreSQL when done with file backups using the SELECT pg_backup_stop() statement
PostgreSQL will write Write-Ahead-Logfiles (WAL) into the WAL Archive directory. These transaction logs contain transactions done while the file backup proceeded
Backup fresh created WAL files
Add files required for a restore backup_label, recovery.signal/recovery.conf (for version <= 12) and tablespace_map (if tablespaces are in use) as virtual files to the backup.
Full Backup tasks performed by the plugin
Incremental backups will only have to backup WAL files created since last reference backup. The postgresql plugin calls pg_switch_wal() to make postgresql create a new WAL file, then all WAL files created since the previous backup are backed up. The plugin receives the postgresql major number, last backup stop time and last LSN from the previous backup and verifies those values. After the backup these values are stored again for the next backup.
Incremental Backup tasks performed by the plugin
The restore basically works like this:
Restore all files to the original PostgreSQL location
Configure PostgreSQL for the recovery (see below)
Start PostgreSQL
PostgreSQL will restore the latest possible consistent point in time. You can manage to restore to any other point in in time available in the WAL files, please refer to the PostgreSQL documentation for more details.
Recovery tasks
Warning
In order to make coherent backups, it is imperative that the same |postgresql| major version is used for full and incremental backups depending on each other.
Prerequisites for the PostgreSQL Plugin
This plugin is a Bareos Python 3 plugin. It requires PostgreSQL cluster version >= 10 and the Python module pg8000 >= 1.16 to be installed.
Since Version >= 21 the plugin was changed to the Python module pg8000, with a required minimum version of 1.16, instead of psycopg2 and using Python >= 3.6 is mandatory.
If a distribution provided pg8000 package exists and is the same or newer version, it can be used. Otherwise it must be installed using the command pip3 install pg8000.
The plugin must be installed on the same host where the PostgreSQL cluster runs, as files are backed up from the local filesystem.
Warning
You have to enable PostgreSQL WAL-Archiving. The process and the plugin depend on it.
As a minimum this requires that you create an WAL archive directory and matching settings in your PostgreSQL configuration file postgresql.conf.
In our examples we assume the WAL archive directory as /var/lib/pgsql/wal_archive/.
...
# wal_level default is replica
wal_level = replica
archive_mode = on
archive_command = 'test ! -f /var/lib/pgsql/wal_archive/%f && cp %p /var/lib/pgsql/wal_archive/%f'
...
Please refer to the PostgreSQL documentation for details.
Note
While the PostgreSQL plugin backups only the required files from the WAL archive directory, old files are not removed automatically.
Installation of the PostgreSQL Plugin
Make sure you have met the prerequisites, after that install the package bareos-filedaemon-postgresql-python-plugin.
Configuration of the PostgreSQL Plugin
Activate your plugin directory in the Bareos File Daemon configuration. See File Daemon Plugins for more about plugins in general.
Now include the plugin as command-plugin in the fileset resource and define a job using this fileset:
You can append options to the plugin call as key=value pairs, separated by :. The following options are available:
- wal_archive_dir
directory where PostgreSQL archives the WAL files as defined in your
postgresql.confwith the archive_command directive. This is a mandatory option, there is no default set.- db_user
with this user the plugin will try to connect to the database. this role should be granted to access all pg_settings and backup functions in the cluster. Default: root
- db_password
a optional password needed for the connection. Default: None
- db_name
there needs to be a named database for the connection. Default: postgres
- db_host
used to specify the host or the socket-directory when starting with a leading /
usually you will set it to /run/postgresql
Default: localhost
- db_port
useful, if cluster is not listening default port. Default: 5432
- ignore_subdirs
a list of comma separated directories below the data_directory, you want to exclude. Default: pgsql_tmp
Note
As recommended by upstream the content of the following sub-directories content will not be backup. But the sub-directory as directory will always be. pg_dynshmem, pg_notify, pg_serial, pg_snapshots, pg_stat_tmp, pg_subtrans, pg_wal
- switch_wal
If set to true (default), the plugin will let PostgreSQL write a new wal file, if the current Log Sequence Number (LSN) is greater than the LSN from the previous job. This makes sure that all changes will be backed up. Default: true
- switch_wal_timeout
Timeout in seconds to wait for WAL archiving after WAL switch: Default 60 seconds
- role
Set the role used after login, before the first sql call. Default: None
- start_fast
By default, the backup will start after a checkpoint which can take some time. If start_fast_start is true, pg_backup_start will be executed as quickly as possible. This enforces an immediate checkpoint which can cause a spike in I/O operations and slowing any concurrently executing queries. Default: False
- stop_wait_wal_archive
Optional parameter of type boolean. It controls if the plugin will wait for the WAL archiving to be complete at the end of the backup. In the default case the plugin will wait. We don’t recommend to change the default here. Default: True
Note
The plugin is using the non-exclusive backup method. Several backups can run at the same time on the cluster: which allow different tools to backup the cluster simultaneously.
For Bareos we recommend to set Allow Duplicate Jobs (Dir->Job)= No
to limit the number of job to only one at the same time.
Restore with the PostgreSQL Plugin
With the usual Bareos restore mechanism a file-hierarchy will be created on the restore client under the default restore location according to the options set:
<restore prefix>/<cluster_data_directory>/<restore prefix>/<wal_archive_dir>/
This example describes how to restore to the latest possible consistent point in time. You can manage to restore to any other point in time available in the WAL files, please refer to the PostgreSQL documentation for more details.
PostgreSQL >= 12
Beginning with PostgreSQL >= 12 the configuration must be done in your PostgreSQL
configuration file postgresql.conf:
...
restore_command = 'cp /var/lib/pgsql/wal_archive/%f %p'
...
Additionally a file named recovery.signal is created in your PostgreSQL datadir by the plugin.
It contains as a comment the backup label jobid and the PostgreSQL major version used.
PostgreSQL < 12
For PostgreSQL < 12 you need to complete the recovery.conf in your PostgreSQL datadir.
It contains as a comment the backup label jobid and the PostgreSQL major version used.
Example:
restore_command = 'cp /var/lib/pgsql/wal_archive/%f %p'
Where /var/lib/pgsql/wal_archive/ is the wal_archive_dir directory.
Initiate the Recovery Process
Make sure that the user postgres is allowed to rename the recovery marker file
(recovery.signal or recovery.conf), as the file needs to be renamed during the
recovery process. Should be the case if restored by the plugin.
You might have to adapt your SELINUX configuration for this.
Starting the PostgreSQL server shall now initiate the recovery process.
Warning
When restoring a cluster which uses tablespaces, the table space location (directory) needs to be empty before the restore. Also ensure that the restored links in data/pg_tblspc point to the restored tablespace data, by default the symlinks will point to the original location.
Warning
We highly advise after a cluster restore, to cleanup older wals than the new history, and trigger as soon as possible a new full backup.
Troubleshooting the PostgreSQL Plugin
If things don’t work as expected, make sure that
the Bareos File Daemon (FD) works in general, so that you can make simple file backups and restores
the Bareos FD Python plugins works in general, try one of the shipped simple sample plugins
check your PostgreSQL data directory for files backup_label recovery.signal tablespace_map. If they exists, the cluster has been restored, but has not been restarted yet.
make sure your dbuser can connect to the database dbname and is allowed to issue the following statements matching your PostgreSQL version:
SELECT current_setting('server_version_num'); SELECT current_setting('archive_mode'); SELECT current_setting('archive_command'); SELECT current_setting('data_directory'); SELECT current_setting('log_directory'); SELECT current_setting('config_file'); SELECT current_setting('hba_file'); SELECT current_setting('identity_file'); SELECT current_setting('ssl_ca_file'); SELECT current_setting('ssl_cert_file'); SELECT current_setting('ssl_crl_file'); SELECT current_setting('ssl_key_file'); SELECT current_setting('ssl_dh_params_file'); SELECT current_setting('ssl_crl_dir'); -- Version >= 15 SELECT pg_backup_start(); SELECT pg_backup_stop(); -- Version >=10 < 15 SELECT pg_start_backup(); SELECT pg_stop_backup(); SELECT pg_current_wal_lsn(); SELECT pg_switch_wal();
Proxmox Plugin
The Proxmox Plugin can be used for agentless backups of virtual machines running on Proxmox Virtual Environment. It is capable of doing full backups of both VM Guests and Container Guests.
It is available since Bareos Version >= 25.0.0.
Status
The Plugin can do full backups and offers two options for restoring them:
It can restore the backup into a new proxmox guest (Virtual Machine / Container).
It can restore the backup into a local vzdump dump file to be recovered later via the proxmox GUI.
Limitation - Proxmox Plugin: Only Full Backups are currently supported.
The Proxmox Plugin currently only supports Full backups.
Requirements
The Proxmox Plugin (together with the Bareos File Daemon) needs to be installed on a member of the proxmox cluster that is running the guests that need to be backed up.
Installation
Start by adding the matching repository according to the following table to one of the Proxmox Virtual Environment cluster members.
Proxmox VE Version |
Bareos Repository to use |
|---|---|
8.x |
Debian_12 |
9.x |
Debian_13 |
Then install the package bareos-filedaemon-proxmox-plugin (using apt) on one of the Proxmox Virtual Environment cluster members. This will automatically also install the Bareos File Daemon and other required packages:
root@proxmox90:~#apt install bareos-filedaemon-proxmox-python-plugin
Installing:
bareos-filedaemon-proxmox-python-plugin
Installing dependencies:
bareos-common bareos-filedaemon-python-plugins-common gawk libmpfr6 libsigsegv2
bareos-filedaemon bareos-filedaemon-python3-plugin libfmt10 libpython3.13 python3-dateutil
Suggested packages:
gawk-doc
Summary:
Upgrading: 0, Installing: 11, Removing: 0, Not Upgrading: 0
Download size: 1,381 kB / 5,184 kB
Space needed: 17.4 MB / 3,892 MB available
Continue? [Y/n] y
Get:1 https://download.bareos.com/bareos/release/25/Debian_13 bareos-common 25.0.0-65 [988 kB]
Get:2 https://download.bareos.com/bareos/release/25/Debian_13 bareos-filedaemon 25.0.0-65 [257 kB]
Get:3 https://download.bareos.com/bareos/release/25/Debian_13 bareos-filedaemon-python-plugins-common 25.0.0-65 [39.2 kB]
Get:4 https://download.bareos.com/bareos/release/25/Debian_13 bareos-filedaemon-python3-plugin 25.0.0-65 [62.4 kB]
Get:5 https://download.bareos.com/bareos/release/25/Debian_13 bareos-filedaemon-proxmox-python-plugin 25.0.0-65 [34.5 kB]
Fetched 1,381 kB in 1s (1,188 kB/s)
[...]
Configuration
Switch the Bareos File Daemon runtime group to root
The Bareos File Daemon is usually running as user root and group bareos.
Unfortunately this does not work on Proxmox Virtual Environment, as it prevents the Bareos File Daemon from backing up the guests.
Running the Bareos File Daemon with the default group bareos leads to the following errors in the job logs:
bareos[...] JobId 1: python3-fd-mod: Executing vzdump 100 --stdout
[...] JobId 1: python3-fd-mod: ipcc_send_rec[1] failed: Unknown error -1
[...] JobId 1: python3-fd-mod: ipcc_send_rec[2] failed: Unknown error -1
[...] JobId 1: python3-fd-mod: ipcc_send_rec[3] failed: Unknown error -1
[...] JobId 1: python3-fd-mod: Unable to load access control list: Unknown error -1
For the bareos proxmox plugin to work properly, the Bareos File Daemon needs to run as user root and group root.
This is achieved by adapting the systemd service to be started as Group root by using
systemctl edit bareos-filedaemon` an adding the following two lines:
[Service]
Group=root
like the following example:
rootsystemctl edit bareos-filedaemon
### Editing /etc/systemd/system/bareos-filedaemon.service.d/override.conf
### Anything between here and the comment below will become the new contents of the file
[Service]
Group=root
### Lines below this comment will be discarded
This will create the file /etc/systemd/system/bareos-filedaemon.service.d/override.conf
containing the lines mentioned above. You can alternatively also create this file directly if desired.
Configure the Bareos File Daemon to load the python plugin
Make sure to add or enable the following settings in your Bareos File Daemon configuration:
Restart the Bareos File Daemon after the changes with systemctl restart bareos-fd. :qk After connectng the client to the director as described in Adding a Client, we go on with configuring jobs and filesets.
Configure jobs and filesets
To define the backup of a VM in Bareos, a job definition and a fileset resource must be added to the Bareos director configuration. In Proxmox Virtual Environment, guests have an unique ID (i.e. a number between 100 - 999999999) that uniquely identifies each guest. The guest ID is visible in the Proxmox Virtual Environment GUI next to the name as can be seen in figure Proxmox Virtual Environment GUI showing the recovered backup .
The following example shows how to configure the backup of the KVM guest with the ID 100 and a Container guest with the ID 101:
The Proxmox plugin automatically detects the different guest types and handles them accordingly. The fileset only differs in the guestid to be backed up, the guest type is neither required nor possible to configure.
Backup of a KVM guest
To run a backup of a KVM guest, simply start the corresponding job proxmox90-vm:
*run job=proxmox90-vm level=Full yes
Using Catalog "MyCatalog"
Job queued. JobId=1
*You have messages.
*messages
[...] bareos-dir JobId 1: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 1: Start Backup JobId 1, Job=proxmox90-vm.2025-11-12_10.21.41_05
[...] bareos-dir JobId 1: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 1: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 1: Connected Client: proxmox90-fd at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 1: Handshake: Immediate TLS
[...] bareos-dir JobId 1: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 1: Using just in time reservation for job 1
[...] bareos-dir JobId 1: Using Device "JustInTime Device" to write.
[...] bareos-sd JobId 1: Connected File Daemon at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] proxmox90-fd JobId 1: Extended attribute support is enabled
[...] bareos-sd JobId 1: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] proxmox90-fd JobId 1: ACL support is enabled
[...] proxmox90-fd JobId 1: Version: 25.0.0~pre1059.ff31e25a9 (10 November 2025) Debian GNU/Linux 13 (trixie)
[...] proxmox90-fd JobId 1: python3-fd-mod: Executing vzdump 100 --stdout
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: starting new backup job: vzdump 100
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: Starting Backup of VM 100 (qemu)
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: Backup started at 2025-11-12 10:21:46
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: status = running
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: include disk 'scsi0' 'local-lvm:vm-100-disk-0' 10G
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: backup mode: snapshot
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: ionice priority: 7
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: sending archive to stdout
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: started backup task 'f8e2c068-679d-43d5-82ef-168887ba4e76'
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: resuming VM again
[...] proxmox90-fd JobId 1: python3-fd-mod: Guest name not set, defaulting to "VM 100"
[...] bareos-sd JobId 1: JustInTime Reservation: Finding drive to reserve.
[...] proxmox90-fd JobId 1: python3-fd-mod: Backing up qemu guest "VM 100" to virtual file PROXMOX/VM 100/vzdump-qemu-100-2025_11_12-10_21_46.vma
[...] bareos-dir JobId 1: Created new Volume "Full-0001" in catalog.
[...] bareos-sd JobId 1: Using Device "File0001" (/var/lib/bareos/storage) to write.
[...] bareos-sd JobId 1: Labeled new Volume "Full-0001" on device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 1: Moving to end of data on volume "Full-0001"
[...] bareos-sd JobId 1: Ready to append to end of Volume "Full-0001" size=223
[...] bareos-dir JobId 1: Max Volume jobs=1 exceeded. Marking Volume "Full-0001" as Used.
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: 23% (2.4 GiB of 10.0 GiB) in 3s, read: 812.0 MiB/s, write: 199.9 MiB/s
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: 40% (4.1 GiB of 10.0 GiB) in 6s, read: 582.4 MiB/s, write: 181.2 MiB/s
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: 65% (6.5 GiB of 10.0 GiB) in 9s, read: 839.8 MiB/s, write: 259.7 MiB/s
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: 92% (9.3 GiB of 10.0 GiB) in 12s, read: 924.4 MiB/s, write: 226.2 MiB/s
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: 100% (10.0 GiB of 10.0 GiB) in 13s, read: 764.2 MiB/s, write: 0 B/s
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: backup is sparse: 7.46 GiB (74%) total zero data
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: transferred 10.00 GiB in 13 seconds (787.7 MiB/s)
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: Finished Backup of VM 100 (00:00:13)
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: Backup finished at 2025-11-12 10:21:59
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: Backup job finished successfully
[...] proxmox90-fd JobId 1: python3-fd-mod: INFO: notified via target `mail-to-root`
[...] proxmox90-fd JobId 1: python3-fd-mod: waiting for command to finish
[...] bareos-sd JobId 1: Releasing device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 1: Elapsed time=00:00:13, Transfer rate=209.9 M Bytes/second
[...] bareos-dir JobId 1: Insert of attributes batch table with 1 entries start
[...] bareos-dir JobId 1: Insert of attributes batch table done
[...] bareos-dir JobId 1: Bareos bareos-dir 25.0.0~pre1327.fd0f53dc3 (31Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 1
Job: proxmox90-vm.2025-11-12_10.21.41_05
Backup Level: Full
Client: "proxmox90-fd" 25.0.0~pre1059.ff31e25a9 (10Nov25) Debian GNU/Linux 13 (trixie),debian
FileSet: "ProxmoxTestVM" 2025-11-12 10:21:41
Pool: "Full" (From Job FullPool override)
Catalog: "MyCatalog" (From Client resource)
Storage: "File" (From Job resource)
Scheduled time: 12-Nov-2025 10:21:41
Start time: 12-Nov-2025 10:21:44
End time: 12-Nov-2025 10:21:59
Elapsed time: 15 secs
Priority: 10
Allow Mixed Priority: no
FD Files Written: 1
SD Files Written: 1
FD Bytes Written: 2,728,973,824 (2.728 GB)
SD Bytes Written: 2,728,974,013 (2.728 GB)
Rate: 181931,6 KB/s
Software Compression: None
VSS: no
Encryption: no
Accurate: no
Volume name(s): Full-0001
Volume Session Id: 1
Volume Session Time: 1762934122
Last Volume Bytes: 2,729,193,300 (2.729 GB)
Non-fatal FD errors: 0
SD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Backup OK
Backup of a Container guest
To backup a container guest, also start the corresponding job proxmox90-ct:
*run job=proxmox90-ct level=Full yes
Job queued. JobId=2
*messages
[...] bareos-dir JobId 2: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 2: Start Backup JobId 2, Job=proxmox90-ct.2025-11-12_12.36.09_04
[...] bareos-dir JobId 2: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 2: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 2: Connected Client: proxmox90-fd at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 2: Handshake: Immediate TLS
[...] bareos-dir JobId 2: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 2: Using just in time reservation for job 2
[...] bareos-dir JobId 2: Using Device "JustInTime Device" to write.
[...] bareos-sd JobId 2: Connected File Daemon at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] proxmox90-fd JobId 2: Extended attribute support is enabled
[...] bareos-sd JobId 2: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] proxmox90-fd JobId 2: ACL support is enabled
[...] proxmox90-fd JobId 2: Version: 25.0.0~pre1059.097ef5ba3 (12 November 2025) Debian GNU/Linux 13 (trixie)
[...] proxmox90-fd JobId 2: python3-fd-mod: Executing vzdump 101 --stdout
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: starting new backup job: vzdump 101
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: Starting Backup of VM 101 (lxc)
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: Backup started at 2025-11-12 12:36:14
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: status = running
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: CT Name: CT101
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: including mount point rootfs ('/') in backup
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: backup mode: snapshot
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: ionice priority: 7
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: create storage snapshot 'vzdump'
[...] proxmox90-fd JobId 2: python3-fd-mod: WARNING: You have not turned on protection against thin pools running out of space.
[...] proxmox90-fd JobId 2: python3-fd-mod: WARNING: Set activation/thin_pool_autoextend_threshold below 100 to trigger automatic extension of thin pools before they get full.
[...] proxmox90-fd JobId 2: python3-fd-mod: Logical volume "snap_vm-101-disk-0_vzdump" created.
[...] proxmox90-fd JobId 2: python3-fd-mod: WARNING: Sum of all thin volume sizes (26.00 GiB) exceeds the size of thin pool pve/data and the amount of free space in volume group (<6.13 GiB).
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: sending archive to stdout
[...] proxmox90-fd JobId 2: python3-fd-mod: Backing up lxc guest "CT101" to virtual file PROXMOX/CT101/vzdump-lxc-101-2025_11_12-12_36_14.vma
[...] bareos-sd JobId 2: JustInTime Reservation: Finding drive to reserve.
[...] bareos-dir JobId 2: Created new Volume "Full-0002" in catalog.
[...] bareos-sd JobId 2: Using Device "File0001" (/var/lib/bareos/storage) to write.
[...] bareos-sd JobId 2: Labeled new Volume "Full-0002" on device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 2: Moving to end of data on volume "Full-0002"
[...] bareos-sd JobId 2: Ready to append to end of Volume "Full-0002" size=223
[...] bareos-dir JobId 2: Max Volume jobs=1 exceeded. Marking Volume "Full-0002" as Used.
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: Total bytes written: 386027520 (369MiB, 30MiB/s)
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: cleanup temporary 'vzdump' snapshot
[...] proxmox90-fd JobId 2: python3-fd-mod: Logical volume "snap_vm-101-disk-0_vzdump" successfully removed.
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: Finished Backup of VM 101 (00:00:13)
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: Backup finished at 2025-11-12 12:36:27
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: Backup job finished successfully
[...] proxmox90-fd JobId 2: python3-fd-mod: INFO: notified via target `mail-to-root`
[...] proxmox90-fd JobId 2: python3-fd-mod: waiting for command to finish
[...] bareos-sd JobId 2: Releasing device "File0001" (/var/lib/bareos/storage).
[...] bareos-sd JobId 2: Elapsed time=00:00:15, Transfer rate=25.73 M Bytes/second
[...] bareos-dir JobId 2: Insert of attributes batch table with 1 entries start
[...] bareos-dir JobId 2: Insert of attributes batch table done
[...] bareos-dir JobId 2: Bareos bareos-dir 25.0.0~pre1327.fd0f53dc3 (31Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 2
Job: proxmox90-ct.2025-11-12_12.36.09_04
Backup Level: Full
Client: "proxmox90-fd" 25.0.0~pre1059.097ef5ba3 (12Nov25) Debian GNU/Linux 13 (trixie),debian
FileSet: "ProxmoxTestCT" 2025-11-12 12:36:09
Pool: "Full" (From Job FullPool override)
Catalog: "MyCatalog" (From Client resource)
Storage: "File" (From Job resource)
Scheduled time: 12-Nov-2025 12:36:09
Start time: 12-Nov-2025 12:36:11
End time: 12-Nov-2025 12:36:28
Elapsed time: 17 secs
Priority: 10
Allow Mixed Priority: no
FD Files Written: 1
SD Files Written: 1
FD Bytes Written: 386,027,520 (386.0 MB)
SD Bytes Written: 386,027,707 (386.0 MB)
Rate: 22707,5 KB/s
Software Compression: None
VSS: no
Encryption: no
Accurate: no
Volume name(s): Full-0002
Volume Session Id: 2
Volume Session Time: 1762947301
Last Volume Bytes: 386,059,314 (386.0 MB)
Non-fatal FD errors: 0
SD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Backup OK
Restoration of a guest to its original guest ID
Restoring a guest to its original guest ID is the easiest way to restore a Proxmox backup.
This is only possible if the guest ID does not exist on the Proxmox Virtual Environment.
If the ID exists, the restore will fail with the message unable to restore VM
100 - VM 100 already exists on node 'proxmox90' or similar.
To restore, select the jobid of the full backup, mark all files for restoration and restore the job to the Proxmox filedaemon:
*restore jobid=1 all done
You have selected the following JobId: 1
[...]
1 file selected to be restored.
Defined Clients:
5: proxmox90-fd
Select the Client (1-6): 5
Plugin Options: *None*
OK to run? (yes/mod/no): yes
Job queued. JobId=5
[...]
* messages
[...] bareos-dir JobId 5: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 5: Start Restore Job RestoreFiles.2025-11-12_12.51.05_09
[...] bareos-dir JobId 5: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 5: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 5: Using Device "File0001" to read.
[...] bareos-dir JobId 5: Connected Client: proxmox90-fd at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 5: Handshake: Immediate TLS
[...] bareos-dir JobId 5: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 5: Connected File Daemon at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 5: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-sd JobId 5: Ready to read from volume "Full-0001" on device "File0001" (/var/lib/bareos/storage).
[...] proxmox90-fd JobId 5: Version: 25.0.0~pre1059.097ef5ba3 (12 November 2025) Debian GNU/Linux 13 (trixie)
[...] proxmox90-fd JobId 5: python3-fd-mod: Executing qmrestore - 100
[...] bareos-sd JobId 5: Forward spacing Volume "Full-0001" to file:block 0:223.
[...] proxmox90-fd JobId 5: python3-fd-mod: restore vma archive: vma extract -v -r /var/tmp/vzdumptmp60261.fifo - /var/tmp/vzdumptmp60261
[...] bareos-sd JobId 5: End of Volume at file 0 on device "File0001" (/var/lib/bareos/storage), Volume "Full-0001"
[...] bareos-sd JobId 5: End of all volumes.
[...] proxmox90-fd JobId 5: python3-fd-mod: CFG: size: 496 name: qemu-server.conf
[...] bareos-sd JobId 5: Releasing device "File0001" (/var/lib/bareos/storage).
[...] proxmox90-fd JobId 5: python3-fd-mod: DEV: dev_id=1 size: 10737418240 devname: drive-scsi0
[...] proxmox90-fd JobId 5: python3-fd-mod: CTIME: Wed Nov 12 12:35:14 2025
[...] proxmox90-fd JobId 5: python3-fd-mod: WARNING: You have not turned on protection against thin pools running out of space.
[...] proxmox90-fd JobId 5: python3-fd-mod: WARNING: Set activation/thin_pool_autoextend_threshold below 100 to trigger automatic extension of thin pools before they get full.
[...] proxmox90-fd JobId 5: python3-fd-mod: Logical volume "vm-100-disk-0" created.
[...] proxmox90-fd JobId 5: python3-fd-mod: WARNING: Sum of all thin volume sizes (18.00 GiB) exceeds the size of thin pool pve/data and the amount of free space in volume group (<6.13 GiB).
[...] proxmox90-fd JobId 5: python3-fd-mod: Logical volume pve/vm-100-disk-0 changed.
[...] proxmox90-fd JobId 5: python3-fd-mod: new volume ID is 'local-lvm:vm-100-disk-0'
[...] proxmox90-fd JobId 5: python3-fd-mod: map 'drive-scsi0' to '/dev/pve/vm-100-disk-0' (write zeros = 0)
[...] proxmox90-fd JobId 5: python3-fd-mod: progress 1% (read 107413504 bytes, duration 0 sec)
[...] proxmox90-fd JobId 5: python3-fd-mod: progress 2% (read 214761472 bytes, duration 1 sec)
[...]
[...] proxmox90-fd JobId 5: python3-fd-mod: progress 97% (read 10415308800 bytes, duration 9 sec)
[...] proxmox90-fd JobId 5: python3-fd-mod: progress 98% (read 10522722304 bytes, duration 9 sec)
[...] proxmox90-fd JobId 5: python3-fd-mod: progress 99% (read 10630070272 bytes, duration 9 sec)
[...] proxmox90-fd JobId 5: python3-fd-mod: progress 100% (read 10737418240 bytes, duration 9 sec)
[...] proxmox90-fd JobId 5: python3-fd-mod: waiting for command to finish
[...] bareos-dir JobId 5: Bareos bareos-dir 25.0.0~pre1327.fd0f53dc3 (31Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 5
Job: RestoreFiles.2025-11-12_12.51.05_09
Restore Client: "proxmox90-fd" 25.0.0~pre1059.097ef5ba3 (12Nov25) Debian GNU/Linux 13 (trixie),debian
Start time: 12-Nov-2025 12:51:07
End time: 12-Nov-2025 12:51:24
Elapsed time: 17 secs
Files Expected: 1
Files Restored: 1
Bytes Restored: 2,728,977,920
Rate: 160528,1 KB/s
FD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Restore OK
The guest has been recovered and can be now be started via commandline or Proxmox Virtual Environment GUI.
While the above example shows the restore of a KVM guest, the procedure to
recover a container guest is slightly different.
When recovering a container backup, the target storage and size need to be
passed via the plugin paramter pctstorage to the plugin in the format
pctstorage=<storagename>\:<size-in-GiB>
Note
This requirement will probably be removed in the next version of the plugin. It is planned to record the original storage and size during the backup and restore to the same recorded values with the option to alter the values during restore.
In the following example, we use local-lvm as storage and 8 as size
which results in the following plugin options:
python:pctstorage=local-lvm\:8
*restore jobid=2 all done
Automatically selected Catalog: MyCatalog
[...]
1 file selected to be restored.
[...]
6: proxmox90-fd
[...]
Select the Client (1-7): 6
Using Catalog "MyCatalog"
Run Restore job
Priority: 10
[...]
Plugin Options: *None*
OK to run? (yes/mod/no): mod
Parameters to modify:
14: Plugin Options
Select parameter to modify (1-14): 14
Please enter Plugin Options string: python:pctstorage=local-lvm\:8
Run Restore job
JobName: RestoreFiles
Priority: 10
Plugin Options: python:pctstorage=local-lvm\:8
[...]
OK to run? (yes/mod/no): yes
Job queued. JobId=4
[...] bareos-dir JobId 4: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-dir JobId 4: Start Restore Job RestoreFiles.2025-11-14_18.12.11_08
[...] bareos-dir JobId 4: Connected Storage daemon at barri-server.bareos:9103, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 4: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 4: Using Device "File0001" to read.
[...] bareos-dir JobId 4: Connected Client: proxmox90-fd at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-dir JobId 4: Handshake: Immediate TLS
[...] bareos-dir JobId 4: Encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 4: Connected File Daemon at proxmox90:9102, encryption: TLS_CHACHA20_POLY1305_SHA256 TLSv1.3
[...] bareos-sd JobId 4: Version: 25.0.0~pre1327.fd0f53dc3 (31 October 2025) AlmaLinux Kitten release 10 (Lion Cub)
[...] bareos-sd JobId 4: Ready to read from volume "Full-0002" on device "File0001" (/var/lib/bareos/storage).
[...] proxmox90-fd JobId 4: Version: 25.0.0~pre1092.5574206a7 (14 November 2025) Debian GNU/Linux 13 (trixie)
[...] bareos-sd JobId 4: Forward spacing Volume "Full-0002" to file:block 0:223.
[...] proxmox90-fd JobId 4: python3-fd-mod: Executing pct restore 101 - --rootfs local-lvm:8
[...] proxmox90-fd JobId 4: python3-fd-mod: WARNING: You have not turned on protection against thin pools running out of space.
[...] proxmox90-fd JobId 4: python3-fd-mod: WARNING: Set activation/thin_pool_autoextend_threshold below 100 to trigger automatic extension of thin pools before they get full.
[...] proxmox90-fd JobId 4: python3-fd-mod: Logical volume "vm-101-disk-0" created.
[...] proxmox90-fd JobId 4: python3-fd-mod: WARNING: Sum of all thin volume sizes (18.00 GiB) exceeds the size of thin pool pve/data and the amount of free space in volume group (<6.13 GiB).
[...] proxmox90-fd JobId 4: python3-fd-mod: Logical volume pve/vm-101-disk-0 changed.
[...] bareos-sd JobId 4: End of Volume at file 0 on device "File0001" (/var/lib/bareos/storage), Volume "Full-0002"
[...] bareos-sd JobId 4: End of all volumes.
[...] bareos-sd JobId 4: Releasing device "File0001" (/var/lib/bareos/storage).
[...] proxmox90-fd JobId 4: python3-fd-mod: Creating filesystem with 2097152 4k blocks and 524288 inodes
[...] proxmox90-fd JobId 4: python3-fd-mod: Filesystem UUID: 6ab7d7e1-0886-40f5-8d66-8fdddeaae664
[...] proxmox90-fd JobId 4: python3-fd-mod: Superblock backups stored on blocks:
[...] proxmox90-fd JobId 4: python3-fd-mod: 32768, 98304, 163840, 229376, 294912, 819200, 884736, 1605632
[...] proxmox90-fd JobId 4: python3-fd-mod: extracting archive from STDIN
[...] proxmox90-fd JobId 4: python3-fd-mod: Total bytes read: 386048000 (369MiB, 243MiB/s)
[...] proxmox90-fd JobId 4: python3-fd-mod: merging backed-up and given configuration..
[...] proxmox90-fd JobId 4: python3-fd-mod: waiting for command to finish
[...] bareos-dir JobId 4: Bareos bareos-dir 25.0.0~pre1327.fd0f53dc3 (31Oct25):
Build OS: AlmaLinux Kitten release 10 (Lion Cub)
JobId: 4
Job: RestoreFiles.2025-11-14_18.12.11_08
Restore Client: "proxmox90-fd" 25.0.0~pre1092.5574206a7 (14Nov25) Debian GNU/Linux 13 (trixie),debian
Start time: 14-Nov-2025 18:12:13
End time: 14-Nov-2025 18:12:21
Elapsed time: 8 secs
Files Expected: 1
Files Restored: 1
Bytes Restored: 386,048,000
Rate: 48256,0 KB/s
FD Errors: 0
FD termination status: OK
SD termination status: OK
Bareos binary info: Bareos pre-release (UNSUPPORTED): Get professional support from https://www.bareos.com
Job triggered by: User
Termination: Restore OK
Overwriting an existing guest with the same ID
- If you want to overwrite an existing guest with the same ID, it is required that:
The existing guest ist powered off
The restore is started with the plugin option force=yes
The options string can be set during the restore in the commandline in option 14: Plugin Options or in the webui in the plugin options field.
Restore to a different guest ID
To restore to a different guest ID, the new guest ID needs to be specified in
the parameter guestid in the “Plugin Options String” during restore:
Restore to .vma dump File
For restoring to local .vma dump file, the Plugin Option restoretodisk=yes must be passed.
The restore will write the dump file into the standard directory for backup
dump files on the proxmox server which is /var/lib/vz/dump
The following example shows how to perform such a restore using bconsole:
*restore jobid=1 all done
Automatically selected Catalog: MyCatalog
Using Catalog "MyCatalog"
You have selected the following JobId: 1
Building directory tree for JobId(s) 1 ...
[...]
Priority: 10
Plugin Options: *None*
OK to run? (yes/mod/no): mod
Parameters to modify:
[...]
9: Bootstrap
10: Where
11: File Relocation
13: JobId
14: Plugin Options
Select parameter to modify (1-14): 14
Please enter Plugin Options string: python:restoretodisk=yes
Run Restore job
JobName: RestoreFiles
Bootstrap: /home/pstorz/git/bareos/root/systemtests/tests/proxmox/working/bareos-dir.restore.1.bsr
Where:
Replace: Always
FileSet: SelfTest
Backup Client: bareos-fd
Restore Client: bareos-fd
Format: Native
Storage: File
When: 2025-09-25 12:12:23
Catalog: MyCatalog
Priority: 10
Plugin Options: python:restoretodisk=yes
OK to run? (yes/mod/no): yes
Job queued. JobId=2
After the backup as been recovered into the default vzdump directory, the backup shows up in the Proxmox GUI and can be recovered just like any other proxmox local backup:

Proxmox Virtual Environment GUI showing the recovered backup
Restore using Bareos WebUI
When using the WebUI to restore a Proxmox Plugin job.
The Bareos WebUI will detect if a plugin based jobs is about to be restored and will
show an additional Plugin options field. Add the required plugin options string here
starting with python: as described above.
Description of all Plugin Options
Note that all plugin options that have been used at backup time, are passed back on restore. Options given on restore will override the values originating from the backup.
- guestid (mandatory on backup)
The ID of the guest to be backed up. On restore it is possible to override this option in order to recreate the guest with a different ID.
example:
python:guestid=999- force (optional)
This allows to overwrite existing guests with the same ID during restore.
example:
python:force=yes- restoretodisk (optional)
Restore to local
.vmavzdump file instead of restoring a guest directly. Default is no.example:
python:restoretodisk=yes- restorepath (optional)
Path where the local
.vmavzdump file will be restored. Default is/var/lib/vzdump.example:
python:restorepath=/var/lib/vzdump/bareos-restores- pctstorage (required during restore of container guests)
Storage and storage size in GiB where the container image will be restored in the format
pctstorage=<storage-name>\:<size-in-GiBPlease not that the colon needs to be escaped with a backslash.
example:
python:pctstorage=local-lvm\:8
Warning
As the colon (:) needs to be escaped with a backslash (\) when passing it as plugin parameter during container restore. This is required because the colon is the delimiter between plugin parameters.
python-fd Plugin
The python-fd plugin behaves similar to the python-dir Plugin. Configuration is done in the FileSet Resource on the Bareos Director and in optional configuration files on the Bareos File Daemon.
Configuration
To load a Python plugin you need
- module_name
The file (or directory) name of your plugin (without the suffix .py)
- module_path
Plugin path (optional, only required when using non default paths)
Plugin specific options can be added as key-value pairs, each pair separated by ’:’ key=value.
Configuration Files
This plugin can handle additional configuration files for the python-based plugins it wraps.
When supplying one or both of the options defaults_file or overrides_file, the supplied value will be treated as a path relative to the Bareos File Daemon configuration. When using a single configuration file instead of a configuration directory, it will be relative to that file’s parent directory. All configuration files will be read on the Bareos File Daemon that executes the job.
Depending on how the file was loaded, the options will have different precedence. When loaded via defaults_file the options in the FileSet will override those from the file. When loaded via overrides_file the options from the file will override those in the FileSet and the ones loaded from a defaults_file. In other words: a defaults_file provides default values that you can override in your FileSet and an overrides_file provides mandatory values that always take precedence.
The configuration files should contain one key-value pair per line that will be used as if they were added to the Plugin (Dir->Fileset->Include) option.
Empty lines or lines starting with semicolon (;), hash (#) or left square bracket ([) will be ignored.
Long values can be split across multiple lines by marking the end-of-line with a backslash (\).
Finally, whitespace around keys, values or continuation lines is discarded.
Note
It is not possible to pass module_path or module_name using a configuration file. The python plugin will be loaded before the plugin options including the configuration files are handled.
Encoded option values
In some cases it is desireable to have option values in an encoded format.
Every option passed to a Python plugin, can be encoded using the supplied script bareos_encode_string.py from the scripts directory.
To use such an encoded value, the option-name must be suffixed with #enc so the plugin knows it needs to decode the value.
Thus, if you previously configured api_key=secret_string you could now configure api_key#enc=b7f<4WprP2baH8KX8.
Python plugin types
We basically distinguish between command-plugin and option-plugins.
Command Plugins
Command plugins are used to replace or extend the FileSet definition in the File Section. If you have a command-plugin, you can use it like in this example:
This example uses the MySQL plugin to backup MySQL dumps.
Option Plugins
Option plugins are activated in the Options resource of a FileSet definition.
Example:
This plugin from https://github.com/bareos/bareos/tree/master/contrib/fd-plugins/bareos_option_example has a method that is called before and after each file that goes into the backup, it can be used as a template for whatever plugin wants to interact with files before or after backup.
Qumulo Python by Yuzuy (Third Party)
The Bareos File Daemon Yuzuy Qumulo plugin is a third party python plugin allowing easy integration of Qumulo clusters with Bareos.
You can learn more about features and usage by consulting Yuzuy Qumulo Backup dedicated page.
Supported features
full backups
incremental backups
fast scan for changed data (no tree walks)
snapshot based backups for consistent file sets
acl support
file and folder exclusions
Virtual Full can be realized with this plugin
Supported versions
Bareos Version >= 22.0.0
Qumulo >= 4.0.0
Using the Qumulo plugin can reduce the run time of backup jobs by magnitudes.
Learn more about Qumulo
VMware Plugin
The VMware Plugin can be used for agentless backups of virtual machines running on VMware vSphere. It makes use of CBT (Changed Block Tracking) to do space efficient full and incremental backups, see below for mandatory requirements.
The plugin consists of two parts. The first part is implemented in Python, it uses the vSphere Web Services API to create and remove snapshots, retrieve VM config metadata, recreate virtual machines and to query CBT data. The second part is the bareos_vadp_dumper which is implemented in C++. This binary uses the Virtual Disk Development Kit (VDDK) to retrieve the virtual disks from the Hypervisor hosts.
It is included in Bareos since Version >= 15.2.0.
Status
The Plugin can do full, differential and incremental backup and restore of VM disks.
Since Version >= 24.0.5 The Plugin can now save and recreate VMs with VirtualSerialPort devices.
Since Version >= 24.0.3 The Plugin can now save and recreate VMs with VirtualUSB devices. Note that VirtualUSB devices could disappear when powering on the VM and the USB device is attached to a different running VM, so a warning message will be emitted when such devices are involved.
Since Version >= 24.0.1 Previous versions of this plugin may have produced incomplete backups, because the CBT information was not retrieved completely in cases where the amount of changes was high, especially differential and incremental jobs were affected more probably. The issue is fixed in this version. To ensure consistent backups, it is recommended to run new full level jobs, as backups taken with previous versions may have an inconsonsistent state when restored.
Since Version >= 23.0.3 the NVRAM of VMs is backed up and restored when recreating a VM to ensure it can boot without issues even when EFI enabled.
Since Version >= 23.0.0 the performance is improved and the cleanup of snapshots is enhanced.
Since Version >= 22.0.0 it also backs up the VM configuration metadata so that it can recreate deleted VMs and then restore the VM disks.
Since Version >= 22.1.0 it is possible to backup and restore VMs which have 2 or more disks on different datastores. See below for related limitations.
Since Version >= 22.1.0 on backup the plugin will retry when taking the snapshot fails, this is configurable by using the options snapshot_retries and snapshot_retry_wait, see below for details.
Current limitations amongst others are:
Limitation - VMware Plugin: Normal VM disks can not be excluded from the backup.
It is not yet possible to exclude normal (dependent) VM disks from backups. However, independent disks are excluded implicitly because they are not affected by snapshots which are required for CBT based backup.
Limitation - VMware Plugin: Restore not possible on recreated VM when VM was created from template or OVA.
When creating a VM from template or OVA, the parameter ddb.adaptertype in the .vmdk file is changed from lsilogic to buslogic although SCSI adapter type is VMware Paravirtual or LSI Logic. Restore works to the same still existing VM, but when such a VM was completely removed so that the plugin recreates it via vSphere API, the newly created disk will have ddb.adaptertype set to lsilogic with different numbers of cylinders and heads which causes the restore to fail due to disk geometry mismatch. Currently there’s no known workaround.
Limitation - VMware Plugin: Restore to different vCenter Server is unsupported.
Restore to a different vCenter Server was not tested, it will probably not work, so it is currently unsupported.
Limitation - VMware Plugin: Incremental or differential backups of disk which migrated to different datastore is currently unsupported.
When a disk of a VM was migrated to a different datastore, the plugin currently cannot handle incremental and differential backups properly. In that case, the plugin will detect it and fail the job. The job log will include an error message saying that full level backup of this job is required. Migrations of disks to other datastores can happen either manually or automatically when storage DRS is enabled.
Limitation - VMware Plugin: Incremental or differential backups of removed and recreated disks or after CBT reset
When a disk of a VM was removed and then added again on the same datastore with the same name, or when a CBT reset happened, then the plugin will detect this and request the full level CBT information, and all allocated blocks of that disk will be backed up in an incremental or differential job as if it were a full level job. The restore of such a job will work, but it will take longer than necessary. The backup will terminate with a warning and a recommendation to run a full level job to optimize restore time.
Since Version >= 23.0.3 the plugin option fallback_to_full_cbt=no (see below) can be used to disable this and terminate the job with failure instead. This can be useful if it is desired to run a new full level job anyway.
Limitation - VMware Plugin: Backup of templates is currently not possible
It is not possible to backup templates, because taking snapshots is not supported on templates, this makes CBT based backups of template impossible.
Requirements
As the Plugin is based on the VMware vSphere Storage APIs for Data Protection, which requires at least a VMware vSphere Essentials License. It is tested against VMware vSphere Storage APIs for Data Protection of VMware 7.0.1. It does not work with standalone unlicensed VMware ESXi™.
Since Bareos Version >= 24.0.5 the plugin is using the Virtual Disk Development Kit (VDDK) 9.0, as of the VDDK 9.0 release notes, it should be compatible with vSphere 9 and the next major release (except new features) and backward compatible with vSphere 7.0.x and 8.0.x, see VDDK release notes at https://techdocs.broadcom.com/us/en/vmware-cis/vsphere/vsphere-sdks-tools/9-0/release-notes/virtual-disk-development-kit/virtual-disk-development-kit-90-release-notes.html for details.
This plugin requires the pyVmomi module version 7.0.2 or greater. Since Bareos Version >= 21.0.0 the package bareos-vmware-plugin no longer includes a dependency on a pyVmomi package, because some Linux distributions don’t provide current versions. Consequently, pyVmomi must be either installed by using pip install pyvmomi or by manually installing a distribution provided pyVmomi package. Generally, the pyVmomi major version should match the used vSphere major version. For available versions see https://pypi.org/project/pyvmomi/
Since Version >= 23.0.3 the plugin requires the modules requests and urllib3 for backup and restore of the NVRAM. There is no dependency in the package. In most Linux distributions, the packages providing these modules can be used. The minimum version of requests must be 2.20.0 and urllib3 must be at least 1.24.1.
If pip install ... returns the message error: externally-managed-environment, it is possible to install the required dependencies only for Bareos Python plugins using the following command:
BPP=$(python3 -c'import sys; print(f"/usr/{sys.platlibdir}/bareos/plugins")')
pip install -t $BPP --upgrade pyvmomi
pip install -t $BPP --upgrade requests
pip install -t $BPP --upgrade urllib3
Note
Installing the requests and urllib3 modules as described above is only necessary when the required versions are not available packaged for the used operating system. See below how to check the installed versions.
The following warning message is not relevant when using the above command, because it installs modules in a path which is not used by system packages:
WARNING: Running pip as the 'root' user can result in broken permissions and conflicting
behaviour with the system package manager. It is recommended to use a virtual environment
Note
It is currently not possible to use Python virtual environments for Bareos Python plugins.
The versions of Python modules which have been installed with the above command can be checked as follows:
BPP=$(python3 -c'import sys; print(f"/usr/{sys.platlibdir}/bareos/plugins")')
pip list --path $BPP
System wide installed Python modules, both packaged and installed using pip, can be listed using the following command:
pip list -v
Installation
Install the package bareos-vmware-plugin including its requirements by using an appropriate package management tool (eg. yum, zypper, apt)
Configuration
First add a user account in vCenter that has full privileges by assigning the account to an administrator role or by adding the account to a group that is assigned to an administrator role. While any user account with full privileges could be used, it is better practice to create a separate user account, so that the actions by this account logged in vSphere are clearly distinguishable. In the future a more detailed set of required role privileges may be defined.
When using the vCenter appliance with embedded SSO, a user account usually has the structure <username>@vsphere.local, it may be different when using Active Directory as SSO in vCenter. For the examples here, we will use bakadm@vsphere.local with the password Bak.Adm-1234.
For more details regarding users and permissions see vSphere documentation at https://techdocs.broadcom.com/us/en/vmware-cis/vsphere/vsphere/8-0/vsphere-security-8-0.html
Make sure to add or enable the following settings in your Bareos File Daemon configuration:
Note: Depending on the platform, the Plugin Directory may also be /usr/lib64/bareos/plugins
To define the backup of a VM in Bareos, a job definition and a fileset resource must be added to the Bareos director configuration. In vCenter, VMs are usually organized in datacenters and folders. The following example shows how to configure the backup of the VM named websrv1 in the datacenter mydc1 folder webservers on the vCenter server vcenter.example.org:
For VMs defined in the root-folder, folder=/ must be specified in the Plugin definition.
Since Bareos Version >= 17.2.4 the module_path is without vmware_plugin directory. On upgrades you either adapt your configuration from
to
or install the bareos-vmware-plugin-compat package which includes compatibility symbolic links.
Since Version >= 17.2.4: The Plugin is using the Virtual Disk Development Kit (VDDK), which requires to pass the thumbprint of the vCenter SSL Certificate since version 6.5. The thumbprint is the SHA1 checksum of the SSL Certificate. The thumbprint can be retrieved like this:
echo -n | openssl s_client -connect vcenter.example.org:443 2>/dev/null | openssl x509 -noout -fingerprint -sha1 | tr -d ":"
The result would look like this:
SHA1 Fingerprint=AABBCCDDEEFF11223344556677889900AABBCCDD
For additional security, there is a now plugin option vcthumbprint, that can optionally be added. It must be given without colons like in the following example:
If the vcthumbprint option is used and the thumbprint on the server changes, for example by renewing or replacing the SSL certificate but not adapting the vcthumbprint parameter in the Bareos configuration, backup jobs will fail and the API will only return an “unknown” error. Since Version >= 22.1.0 the plugin will compare the configured thumbprint with the server thumbprint and emit an appropriate error message and advice to update vcthumbprint parameter.
For ease of use (but less secure) when the vcthumbprint is not given, the plugin will retrieve the thumbprint.
Also since Version >= 17.2.4 another optional plugin option has been added that can be used for trying to force a given transport method. Normally, when no transport method is given, VDDK will negotiate available transport methods and select the best one. For a description of transport methods, see
When the plugin runs in a VMware virtual machine which has access to datastore where the virtual disks to be backed up reside, VDDK will use the hotadd transport method. On a physical server without SAN access, it will use the NBD transport method, hotadd transport is not available in this case.
To try forcing a given transport method, the plugin option transport can be used, for example
Note that the backup will fail when specifying a transport method that is not available.
Since Version >= 17.2.8 it is possible to use non-ascii characters and blanks in the configuration for folder and vmname. Also virtual disk file names or paths containing non-ascii characters are handled correctly now. For backing up VMs that are contained in vApps, it is now possible to use the vApp name like a folder component. For example, if we have the vApp named
Test vApp in the folder /Test/Test Folder and the vApp contains the two VMs Test VM 01 and Test VM 02, then the configuration of the filesets should look like this:
However, it is important to know that it is not possible to use non-ascii characters as an argument for the Name of a job or fileset resource.
Since Version >= 20 it is optionally possible to use a configuration file on the system running the Bareos File Daemon. This can be useful to specify common plugin options instead of having to repeat them in every Fileset. Options which are specifed in the config file will override options from the Fileset, if the same option is given there, too. A warning will be issued in that case. Use the plugin option config_file to specify the config file name as in the following example:
And the config file as follows:
Note
Do not use quotes in the above config file, it is processed by the Python ConfigParser module and the quotes would not be stripped from the string.
Since Version >= 20 To allow backing up VMs which do not support quiesced snapshots, it is now possible to use the plugin option quiesce. By default quiescing when not explicitly using this option, quiescing is enabled to create backups that are as consistent as possible. When setting quiesce=no it is more likely to backup an inconsistent state. In this case, the backup job log will contain an appropriate warning and the the job termination will be Backup OK – with warnings.
Quiescing on Windows VMs also triggers VSS snapshot when VMware Tools are installed. If that fails for example on MS SQL Server, it can help to disable VSS application quiescing using the VMware Tools configuration by adding this to the VMware Tools config:
For details see https://knowledge.broadcom.com/external/article?legacyId=2146204
It is also possible to disable specific VSS writers with VMware Tools. The article https://knowledge.broadcom.com/external/article?legacyId=1031200 describes how to check VSS writer errors and how to disable specific VSS writers in the VMware Tools configuration.
For consistent backups of MS SQL server, please use the Bareos MSSQL Plugin.
Backup
Before running the first backup, CBT (Changed Block Tracking) must be enabled for the VMs to be backed up.
Since Version >= 22.1.1 the plugin will try to enable CBT automatically when the plugin option enable_cbt=yes is set (see below). Since Version >= 23.0.0 this option is set to yes by default.
As of https://knowledge.broadcom.com/external/article?legacyId=2075984 manually enabling CBT is currently not working properly. The API however works properly. To enable CBT use the Script vmware_cbt_tool.py, it is packaged in the bareos-vmware-plugin package:
user@host:~$ vmware_cbt_tool.py --help
usage: vmware_cbt_tool.py [-h] -s HOST [-o PORT] -u USER [-p PASSWORD] -d
DATACENTER [-f FOLDER] [-v VMNAME]
[--vm-uuid VM_UUID] [--enablecbt] [--disablecbt]
[--resetcbt] [--info] [--listall] [--sslverify]
[--dumpvmconfig]
Process args for enabling/disabling/resetting CBT
optional arguments:
-h, --help show this help message and exit
-s HOST, --host HOST Remote host to connect to
-o PORT, --port PORT Port to connect on
-u USER, --user USER User name to use when connecting to host
-p PASSWORD, --password PASSWORD
Password to use when connecting to host
-d DATACENTER, --datacenter DATACENTER
DataCenter Name
-f FOLDER, --folder FOLDER
Folder Name (must start with /, use / for root folder
-v VMNAME, --vmname VMNAME
Names of the Virtual Machines
--vm-uuid VM_UUID Instance UUIDs of the Virtual Machines
--enablecbt Enable CBT
--disablecbt Disable CBT
--resetcbt Reset CBT (disable, then enable)
--info Show information (CBT supported and enabled or
disabled)
--listall List all VMs in the given datacenter with UUID and
containing folder
--sslverify Force SSL certificate verification
--dumpvmconfig Dump VM config metadata to JSON file
Note
The options --vm-uuid and --listall have been added in version Version >= 17.2.8, the tool is also able now to process non-ascii character arguments for the --folder and --vmname arguments and vApp names can be used like folder name components.
With --listall all VMs in the given datacenter are reported in a tabular output including instance UUID and containing Folder/vApp name.
Without the option --sslverify also self-signed SSL certificates will be accepted, but a warning message will be emitted in this case.
The option --dumpvmconfig is helpful to debug issues with the transformation of VM config metadata for recreating virtual machines. The JSON file will be written to the current working directory when this option is used.
For the above configuration example, the command to enable CBT would be
user@host:~$ vmware_cbt_tool.py -s vcenter.example.org -u bakadm@vsphere.local -p Bak.Adm-1234 -d mydc1 -f /webservers -v websrv1 --enablecbt
Note: CBT does not work if the virtual hardware version is 6 or earlier.
After enabling CBT, Backup Jobs can be run or scheduled as usual, for example in bconsole:
run job=vm-websrv1 level=Full
Restore
For restoring to the same still exising VM from which the backup has been taken, the VM must be powered off and no snapshot must exist. In bconsole use the restore menu 5, select the correct FileSet and enter mark *, then done. After restore has finished, the VM will be set to its previous powerstate. So if it was powered on at backup time, it will be powered on after restore. This can be changed by using the plugin option restore_powerstate (see below).
Since Version >= 22.0.0 the plugin will recreate the VM if it does not exist. By passing plugin options, with this version it is also possible to recreate the VM in a different folder, datacenter, host, cluster, resource pool or datastore, see below for details. The MAC address and the UUID of the VM will be restored, too. Restoring to a different VM location, eg, by passing a different folder, will create a new VM even if the VM which was backed up still exists. In this case, the new VM will get a new generated MAC address and UUID.
Note
When restoring a VM to a different location while the backed up VM still exists and a static IP is configured within the VM: To avoid IP address conflicts, make sure to also add the plugin option restore_powerstate=off and disable or change the network adapter configuration of the VM before powering it on.
To restore to a different folder, datacenter, host, cluster, resource pool or datastore, the corresponding plugin options must be passed. All plugin options which have been effective at backup time will be passed on restore and each individual option can be overridden by passing an options string at restore time. For example, to restore to a different VM name and different datastore, pass the following plugin option string:
python:datastore=datastore2:vmname=testvm1restored
All other plugin options which are not passed explicitily on restore will be the same as at backup time.
Note that most plugin options are used for backup and restore, but there are some which can be only used on restore, for example to prevent from powering on the VM automatically after restore if it was powered on at backup time, use this plugin options string:
python:restore_datastore=datastore2:vmname=testvm1restored:restore_powerstate=off
See below for a complete restore example and description of all plugin options.
Restore using Bareos WebUI
Since Version >= 22.0.0 it is possible to use the Bareos WebUI to restore VMware Plugin jobs.
When using the WebUI to restore a VMware Plugin job, it is important to set Merge all client file sets to no and Merge all jobs up to the last full backup together to yes. In the File selection all files must be selected. Only restoring selected virtual disks will probably not work and is currently unsupported. The Bareos WebUI will detect if a plugin based jobs is restore and will then show an additional Plugin options field, here a plugin options string starting with python: as described above can be entered.
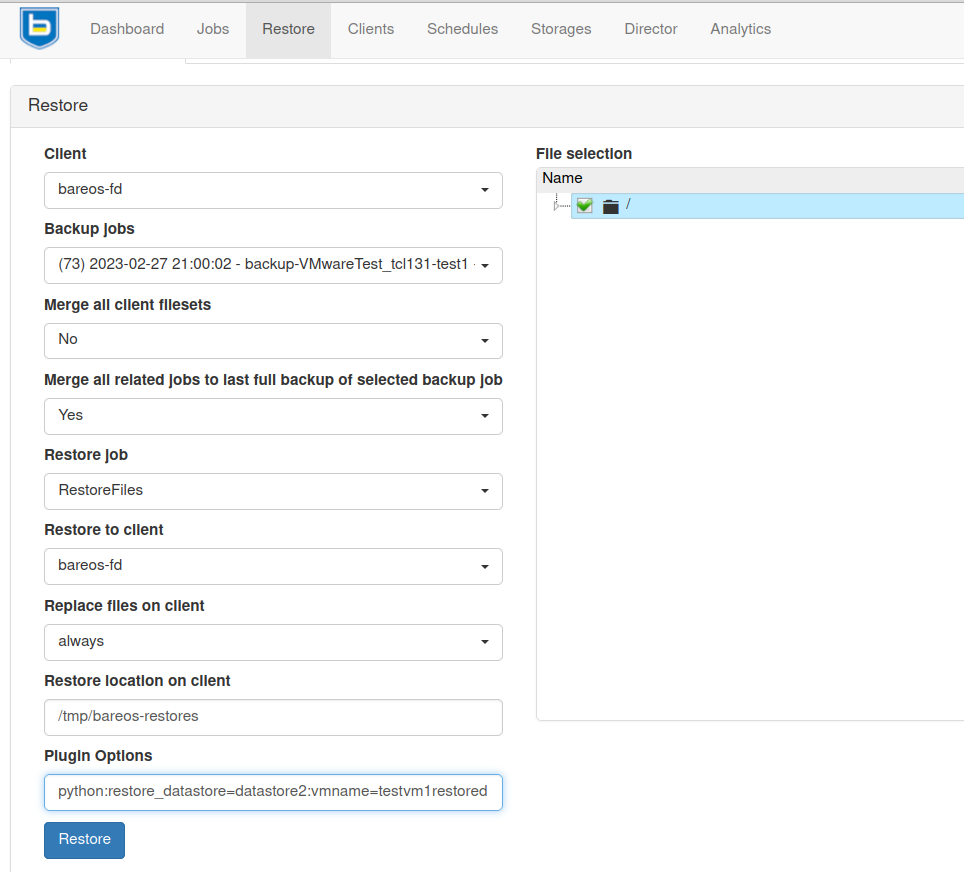
Restore to local VMDK File
Since Version >= 15.2.3 it is possible to restore to local VMDK files. That means, instead of directly restoring a disk that belongs to the VM, the restore creates VMDK disk image files on the filesystem of the system that runs the Bareos File Daemon. As the VM that the backup was taken from is not affected by this, it can remain switched on while restoring to local VMDK. Such a restored VMDK file can then be uploaded to a VMware vSphere datastore or accessed by tools like guestfish to extract single files.
For restoring to local VMDK, the plugin option localvmdk=yes must be passed. The following example shows how to perform such a restore using bconsole:
*restore
Automatically selected Catalog: MyCatalog
Using Catalog "MyCatalog"
First you select one or more JobIds that contain files
to be restored. You will be presented several methods
of specifying the JobIds. Then you will be allowed to
select which files from those JobIds are to be restored.
To select the JobIds, you have the following choices:
1: List last 20 Jobs run
...
5: Select the most recent backup for a client
...
13: Cancel
Select item: (1-13): 5
Automatically selected Client: vmw5-bareos-centos6-64-devel-fd
The defined FileSet resources are:
1: Catalog
...
5: PyTestSetVmware-test02
6: PyTestSetVmware-test03
...
Select FileSet resource (1-10): 5
+-------+-------+----------+---------------+---------------------+------------------+
| jobid | level | jobfiles | jobbytes | starttime | volumename |
+-------+-------+----------+---------------+---------------------+------------------+
| 625 | F | 4 | 4,733,002,754 | 2016-02-18 10:32:03 | Full-0067 |
...
You have selected the following JobIds: 625,626,631,632,635
Building directory tree for JobId(s) 625,626,631,632,635 ...
10 files inserted into the tree.
You are now entering file selection mode where you add (mark) and
remove (unmark) files to be restored. No files are initially added, unless
you used the "all" keyword on the command line.
Enter "done" to leave this mode.
cwd is: /
$ mark *
10 files marked.
$ done
Bootstrap records written to /var/lib/bareos/vmw5-bareos-centos6-64-devel-dir.restore.1.bsr
The job will require the following
Volume(s) Storage(s) SD Device(s)
===========================================================================
Full-0001 File FileStorage
...
Incremental-0078 File FileStorage
Volumes marked with "*" are online.
10 files selected to be restored.
Using Catalog "MyCatalog"
Run Restore job
JobName: RestoreFiles
Bootstrap: /var/lib/bareos/vmw5-bareos-centos6-64-devel-dir.restore.1.bsr
Where: /tmp/bareos-restores
Replace: Always
FileSet: Linux All
Backup Client: vmw5-bareos-centos6-64-devel-fd
Restore Client: vmw5-bareos-centos6-64-devel-fd
Format: Native
Storage: File
When: 2016-02-25 15:06:48
Catalog: MyCatalog
Priority: 10
Plugin Options: *None*
OK to run? (yes/mod/no): mod
Parameters to modify:
1: Level
...
14: Plugin Options
Select parameter to modify (1-14): 14
Please enter Plugin Options string: python:localvmdk=yes
Run Restore job
JobName: RestoreFiles
Bootstrap: /var/lib/bareos/vmw5-bareos-centos6-64-devel-dir.restore.1.bsr
Where: /tmp/bareos-restores
Replace: Always
FileSet: Linux All
Backup Client: vmw5-bareos-centos6-64-devel-fd
Restore Client: vmw5-bareos-centos6-64-devel-fd
Format: Native
Storage: File
When: 2016-02-25 15:06:48
Catalog: MyCatalog
Priority: 10
Plugin Options: python: module_path=/usr/lib64/bareos/plugins:module_name=bareos-fd-vmware: dc=dass5:folder=/: vmname=stephand-test02: vcserver=virtualcenter5.dass-it:vcuser=bakadm@vsphere.local: vcpass=Bak.Adm-1234: localvmdk=yes
OK to run? (yes/mod/no): yes
Job queued. JobId=639
Note: Since Bareos Version >= 15.2.3 it is sufficient to add Python plugin options, e.g. by
Before, all Python plugin must be repeated and the additional be added, like:
After the restore process has finished, the restored VMDK files can be found under path{/tmp/bareos-restores/}:
$ <input>ls -laR /tmp/bareos-restores</input>
/tmp/bareos-restores:
total 28
drwxr-x--x. 3 root root 4096 Feb 25 15:47 .
drwxrwxrwt. 17 root root 20480 Feb 25 15:44 ..
drwxr-xr-x. 2 root root 4096 Feb 25 15:19 [ESX5-PS100] stephand-test02
$ <input>ls -la "/tmp/bareos-restores/[ESX5-PS100] stephand-test02"</input>
/tmp/bareos-restores/[ESX5-PS100] stephand-test02:
total 7898292
drwxr-xr-x. 2 root root 4096 Feb 25 15:19 .
drwxr-x--x. 3 root root 4096 Feb 25 15:47 ..
-rw-------. 1 root root 2075197440 Feb 25 15:19 stephand-test02_1.vmdk
-rw-------. 1 root root 6012731392 Feb 25 15:19 stephand-test02.vmdk
Description of all Plugin Options
Note that all plugin options that have been used at backup time, are passed on restore. The VM metadata is saved in restoreobjects both in the catalog DB and volume, it is used on restore if the VM must be recreated. Most options are used for both backup and restore, some which can be only used for restore start with restore_. Where nothing special is mentioned regarding restore, it is normally not necessary or useful to override that option on restore.
- vcserver (mandatory on backup)
Hostname (FQDN) or IP address of vCenter server. Restore to different vCenter Server is unsupported.
- vcuser (mandatory on backup)
Username for API access to vCenter, eg. administrator@vsphere.local
- vcpass (mandatory on backup)
Password for API access to vCenter
- dc (mandatory on backup)
Datacenter name. This can be optionally passed on restore to recreate the VM in a different datacenter. If the datacenter is not located in the root folder, it is required to specify the full path including the datacenter name starting with the slash character, for example
dc=/My DC Folder/mydc1.- folder (mandatory on backup)
The VM folder in which the VM to be backed up resides. This must be given like a UNIX path with
/as separator. On restore if defined will recreate the VM in a different folder. The given folder must exist before starting the restore.- vmname (mandatory on backup)
The name of the VM to be backed up. On restore it is possible to override this option in order to recreate the VM with a different name.
- vcthumbprint (optional)
Thumbprint of the vCenter SSL Certificate, which is the SHA1 checksum of the SSL Certificate
- transport (optional)
Normally the transport mode mode will be autonegotiated, eg. if the system that runs this plugin is a VM has storage access to the datastore of the VM that’s being backed up, the hotadd transport will be used. Otherwise the nbd or nbdssl transport. For details about transport modes see the VDDK documentation. This option can be used to force the given transport mode.
- log_path (optional)
The default log path is
/var/log/bareos/. A different path can be specified using this option, it will be used forbareos_vadp_dumperlog files.- localvmdk (optional)
Restore to local
.vmdkfile(s) instead of restore to VM. Default is no.- vadp_dumper_verbose (optional)
When setting
vadp_dumper_verbose=yes, the option-vwill be added when runningbareos_vadp_dumper. This can be helpful for debugging purposes.- verifyssl (optional)
By default the validity of SSL certificates will be verified. By setting
verifyssl=nothis can be disabled.- quiesce (optional)
The backed up VM will be triggered to quiesce its filesystems before creating a snapshot by default to increase the data consistency. This can fail or take very long on a VM which runs heavy I/O workload. When setting
quiesce=nothe quiescing will be skipped, but the snapshot may be inconsistent. It is not recommended to use this option, instead try stop heavy I/O load before snapshot. This could be possible by running pre-freeze and post-thaw actions which can be configured in VMware tools, see VMware documentation for details.- cleanup_tmpfiles (optional)
By default, temporary files created by the plugin will be cleaned up after backup or restore. When setting
cleanup_tmpfiles=nothey will be left over, this can be helpful for debugging purposes. Since Version >= 22.0.0- restore_esxhost (optional)
By default, if a VM to be restored does not exist, it will be recreated on the same host that it has been running on at backup time. Use this option to restore on the given ESX host. Since Version >= 22.0.0
- restore_cluster (optional)
Instead of specifying restore_esxhost, it is also possible to specify a cluster name using this option, the ESX host will be autoselected in that case, if DRS is configured properly. Since Version >= 22.0.0
- restore_datastore (optional)
By default, if a VM to be restored does not exist, it will be recreated in the same datastore where it was stored at backup time. Use this option to restore on the given datastore. Since Version >= 22.0.0. As Version >= 22.1.0 it is possible to backup and restore VMs with disks on multiple datastores, when using this option, it will only change the datastore of the disks which were stored in the same datastore as the VM, the other disks will be recreated on the same datastore they were backed up from.
- restore_resourcepool (optional)
By default, if a VM to be restored does not exist, it will be recreated in the same resource pool which it has in been in at backup time. Using this option allows to override this and specify a different resource pool. Since Version >= 22.0.0
- restore_powerstate (optional)
By default, after restore a VM will be set to its previous powerstate which means the powerstate at backup time. When specifying
restore_powerstate=offthe VM will stay powered off after restore. Also can be forced to on withrestore_powerstate=on. Note that this will only work if DRS is configured to fully automated, otherwise the API request to power on a VM will be ignored. Since Version >= 22.0.0- snapshot_retries (optional)
Number of retries when taking a snapshot fails (default: 3). The most common cause of snapshot failure is “error while quiescing the virtual machine”. In this case usually retrying helps. If not, also check if a pre-freeze script is used on the VM, as a non-zero exit code will cause a quiescing error. The pre-freeze and post-thaw scripts are executed by VMwareTools. Since Version >= 22.1.0
- snapshot_retry_wait (optional)
Time in seconds to wait before the next snapshot retry (default: 5). Since Version >= 22.1.0
- poweron_timeout (optional)
Timeout in seconds to wait for a VM to be powered on after restore, default 15s. When a VM is powered on after restore (see also the option restore_powerstate above), the plugin will check if it succeeded by checking the power state. If it is not powered on within this timeout, the restore job will issue a warning message.
- enable_cbt (optional)
When using
enable_cbt=yes, the plugin will enable CBT (changed block tracking) if possible and it is not yet enabled. It is required that no snapshot exists when enabling CBT, otherwise the plugin will emit an error message. By default this option is set to yes since Version >= 23.0.0 so thatvmware_cbt_tool.pyis no longer necessary to enable CBT. This option exists since Version >= 22.1.1- do_io_in_core (optional)
With the option
do_io_in_core=yesthe data stream from the bareos_vadp_dumper will be processed directly by the Bareos core via file descriptor. When set to no, the data stream is read and written by the Python plugin code from the file descriptor and exchanged with the core over a buffer. So enabling this can improve the performance and will save CPU resource consumption. See Python Plugin API for more details. By default this is set to yes. Since Version >= 23.0.0- vadp_dumper_multithreading (optional)
The option
vadp_dumper_multithreading=yesenables multithreading when running bareos_vadp_dumper, so that it will run one reader and one writer thread. By default it is set to yes as nowadays CPUs usually have multiple cores, so this improves the performance in most cases. Since Version >= 23.0.0- vadp_dumper_sectors_per_call (optional)
This option can be used to optimize the performance. The default value it is set to 16384. This is the smallest value that achieved the maximum throughput in our benchmark tests. Together with
vadp_dumper_multithreading=yesthis setting can improve the backup performance significantly. Since Version >= 23.0.0- vadp_dumper_query_allocated_blocks_chunk_size (optional)
The bareos_vadp_dumper uses a VDDK function to query the allocated blocks of virtual disks since Version >= 23.0.0. Especially for full backups, this normally leads to smaller and implicitly faster backups. By setting this plugin option, the chunk size which is passed to that function can be set. The default value for the chunk size is 1024. Allowed values are powers of two between 128 and 131072, inclusive. In our benchmark tests with small VMs of 3GB size, this value did not have any performance impact. However, with more data it might have an impact on the backup performance.
- fallback_to_full_cbt (optional)
In some situations requesting the CBT information for an incremental backup can fail, for example when the CBT information had to be reset. In that case, by default the plugin will fall back to request full level CBT information, which leads to a successful incremental backup job, but it will have the size of a full level backup job. As a consequence, restore time would increase, so a warning will be emitted in the job log, recommending a new full level backup. By setting
fallback_to_full_cbt=no, the job will not request full level CBT and terminate immediately with failure instead. This can be used if it is desired to run a subsequent new full level backup. Note that this does not happen automatically, a new full level job must be run manually afterwards, but this can be automated by using a post backup script, for details see https://github.com/bareos/bareos/tree/master/contrib/misc/reschedule_job_as_fullSince Version >= 23.0.3
- restore_allow_disks_mismatch (optional)
When using VSAN, restoring with recreating the VM can fail because the plugin detects a disk mismatch, as when using VSAN obviously recreated disks get a generated backing disk path. When passing the plugin option
restore_allow_disks_mismatch=yes, this disk match check will allow a mismatch and continue the restore. This option will only be used when recreating the VM to be restored.Since Version >= 23.0.4
- nvram_connect_timeout (optional)
When backing up or restoring NVRAM, this is done by HTTPS connection to the vCenter server. The connect timeout in seconds can be changed using this parameter, the default is 30s.
Since Version >= 25.0.5
- nvram_readwrite_timeout (optional)
When backing up or restoring NVRAM, this is done by reading or writing it via HTTPS connection to/from the vCenter server. The timeout in seconds can be changed using this parameter, the default is 60s.
Since Version >= 25.0.5
- uuid (deprecated)
The uuid option could be used instead of dc, folder and vmname to uniquely address a VM for backup. As the plugin since Version >= 22.0.0 is able recreate VMs in a different datacenter, folder or datastore, this option has become useless. When using uuid, restoring is only possible to the same still existing VM. It is recommended to change the configuration, as the uuid option will be dropped in the next version.